Network security cont. #
RSA cont. #


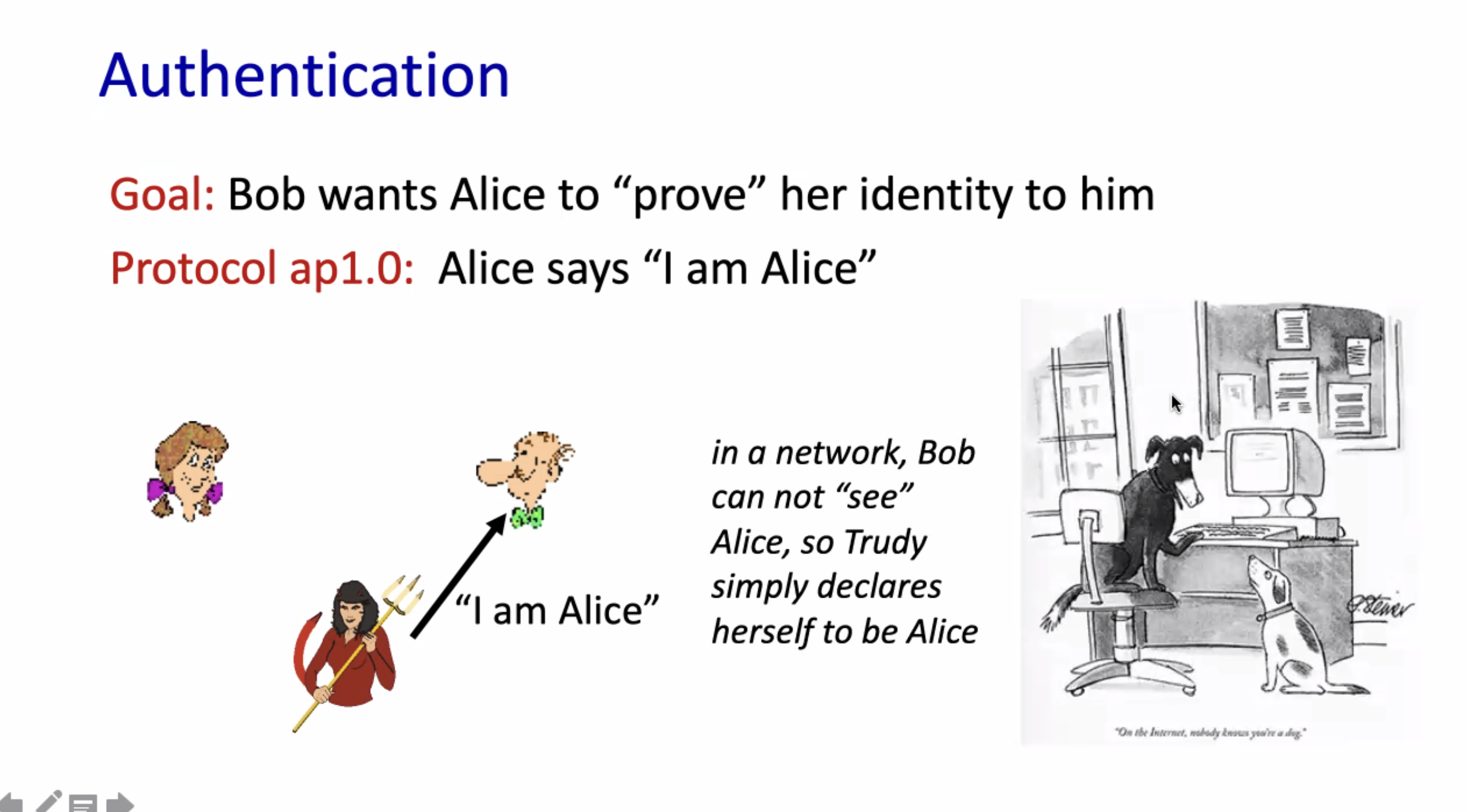
Authentication #


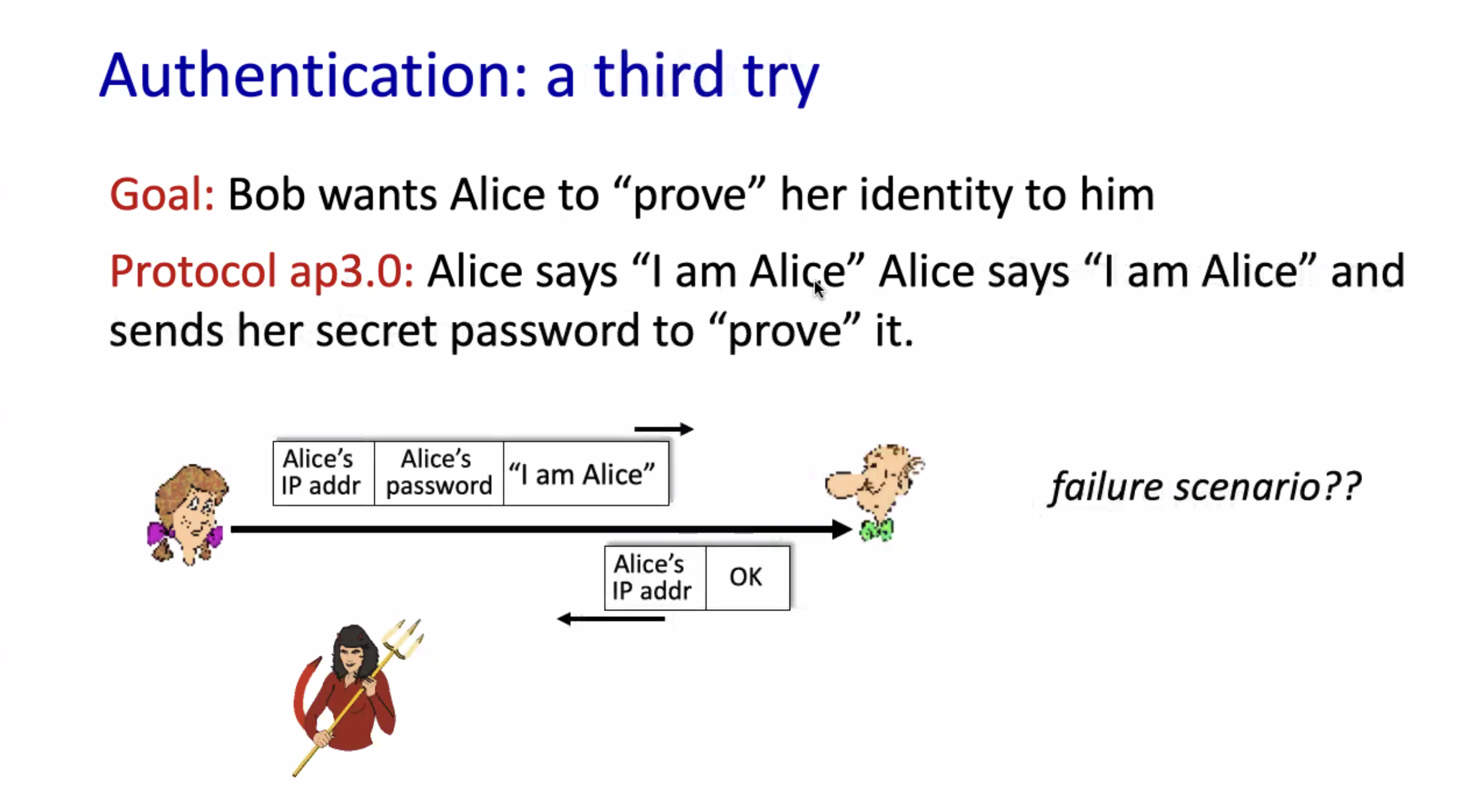
ap = authentication protocol (fictional)
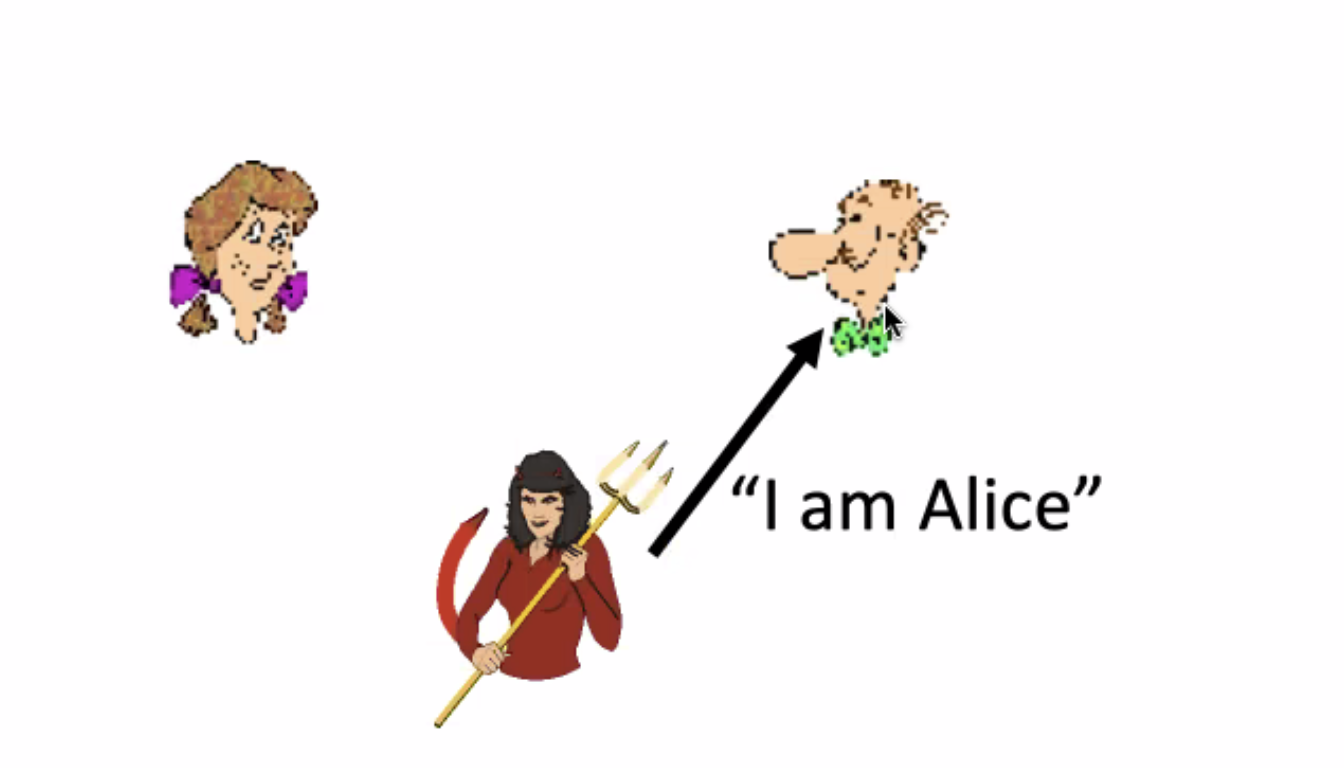

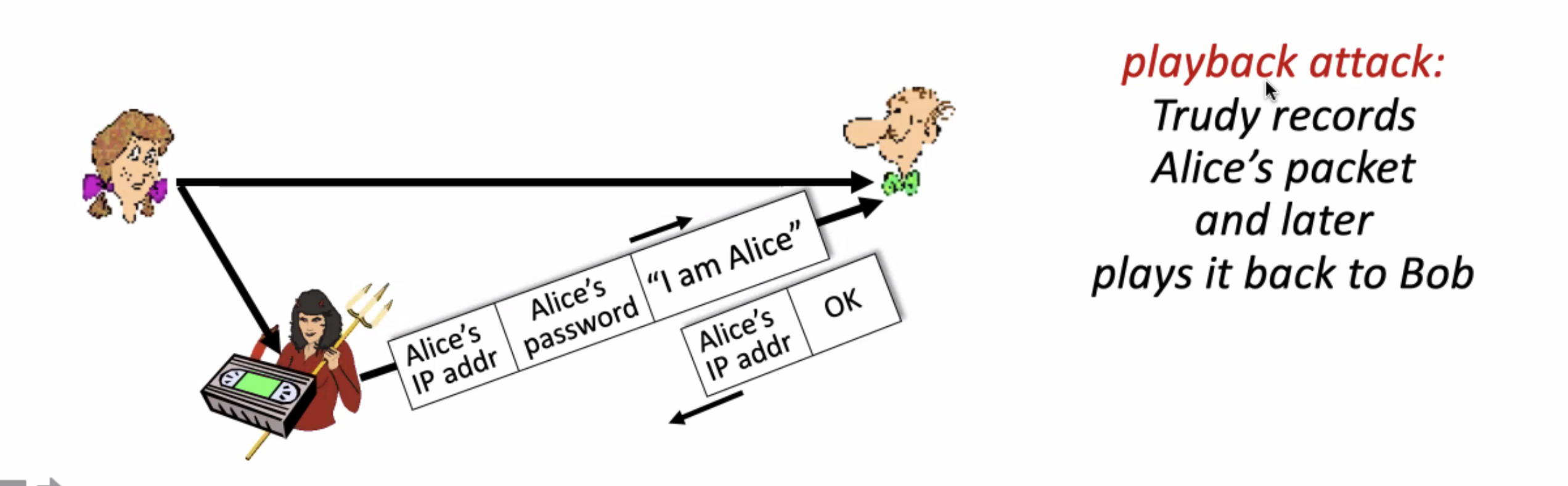
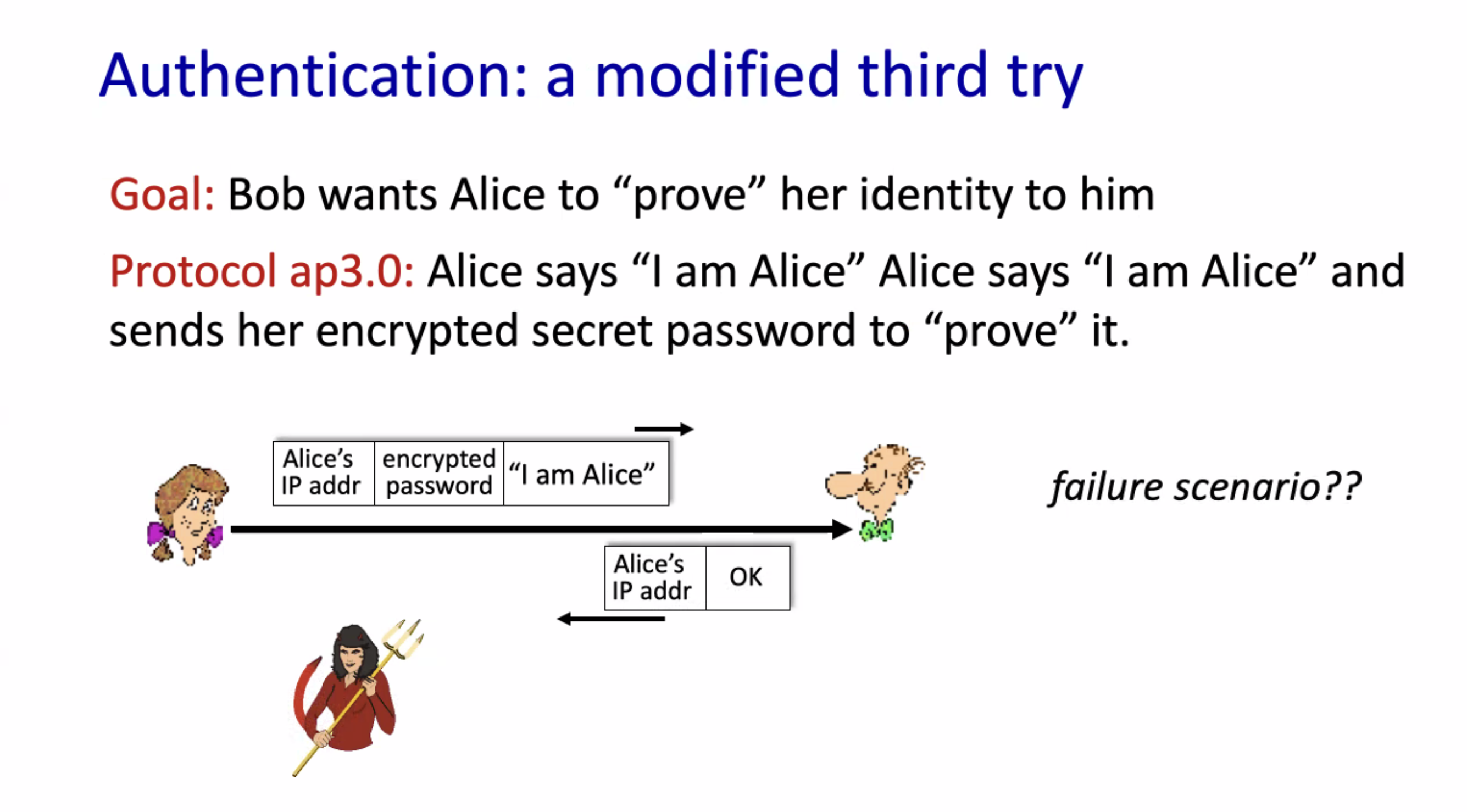
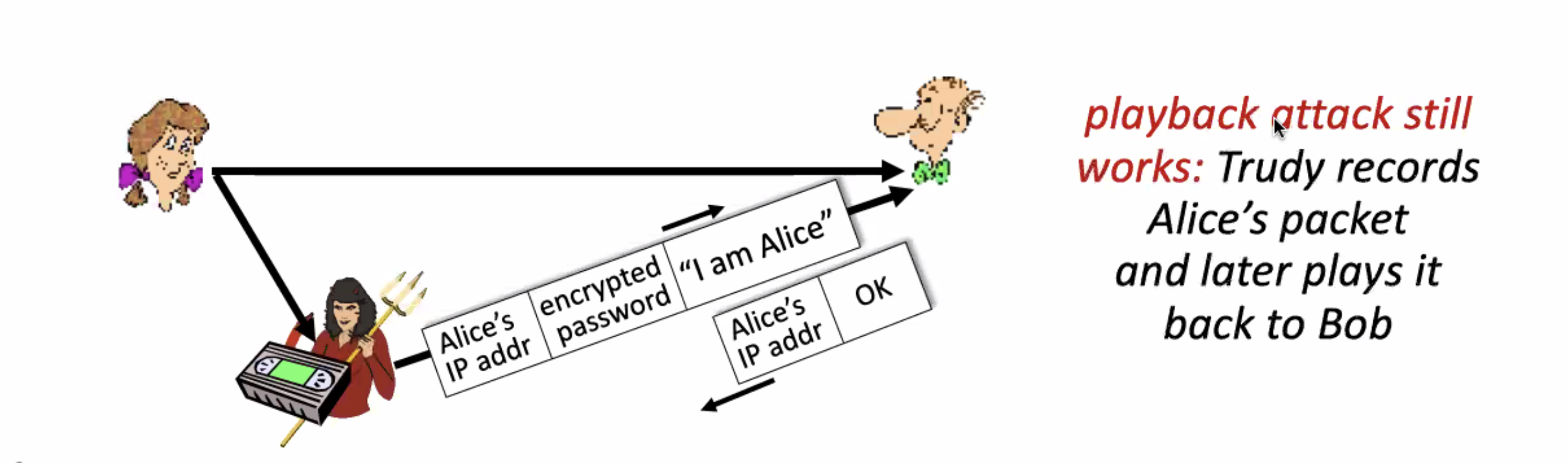
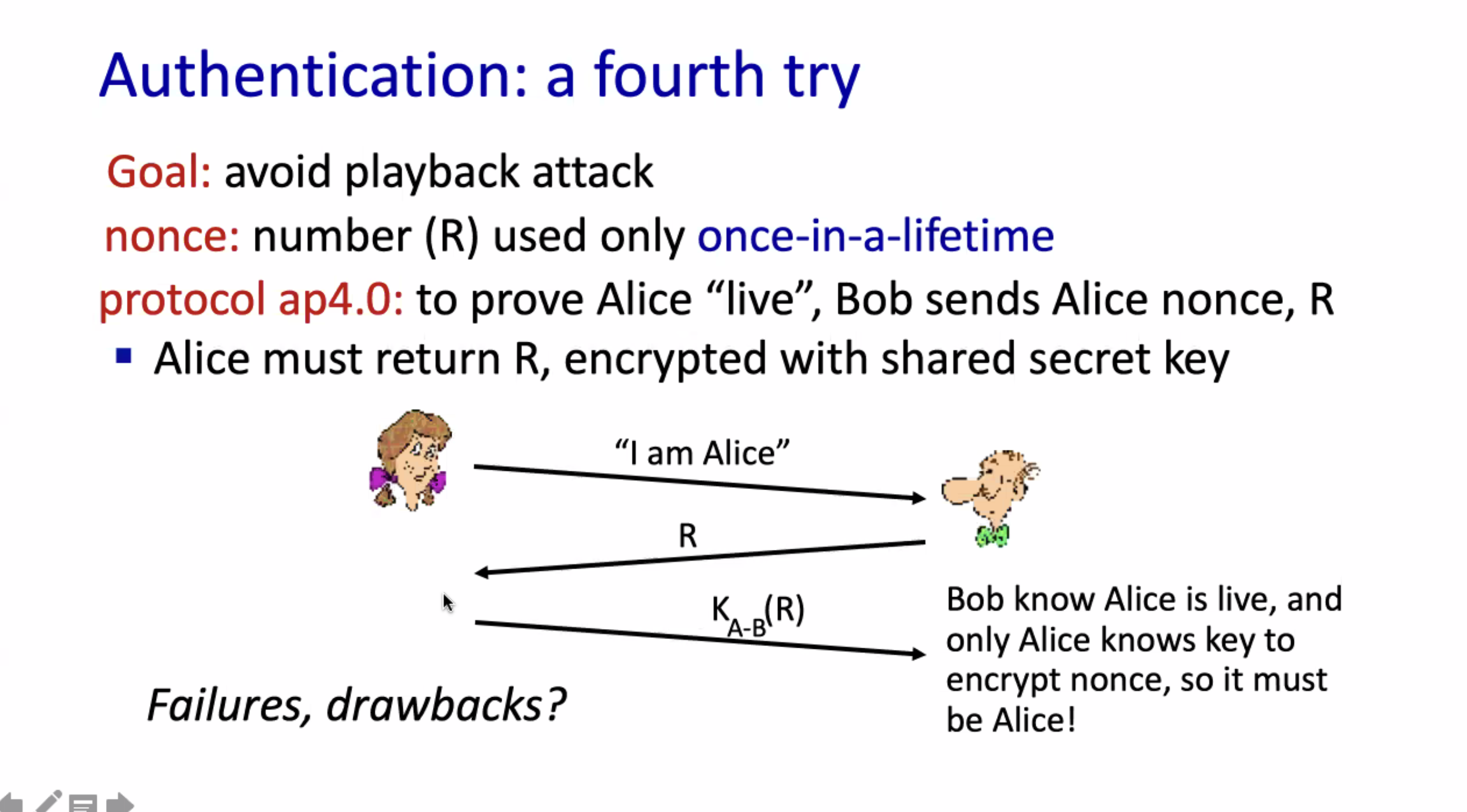
Challenge-response mechanism for authentication:
- Using symmetric shared key,
\( K_{ab} \)
- Alice sends the message to bob saying “I am alice”
- Bob generates a random one-time use nonce, and encrypts it with the shared key \( R = K_{ab}(\text{nonce}) \)
- Alice decrypts \( R \) based on the symmetric key \( K_{ab} \) . Alice sends the result to Bob.
- Bob matches the response, if it matches then it authenticates Alice.
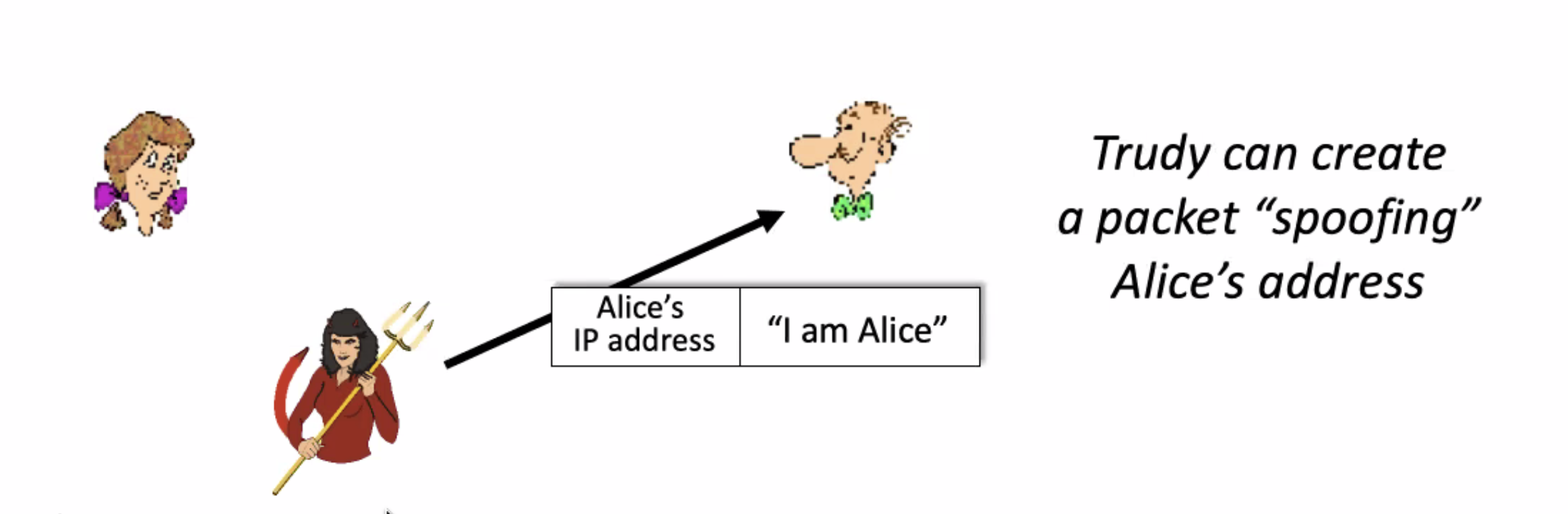
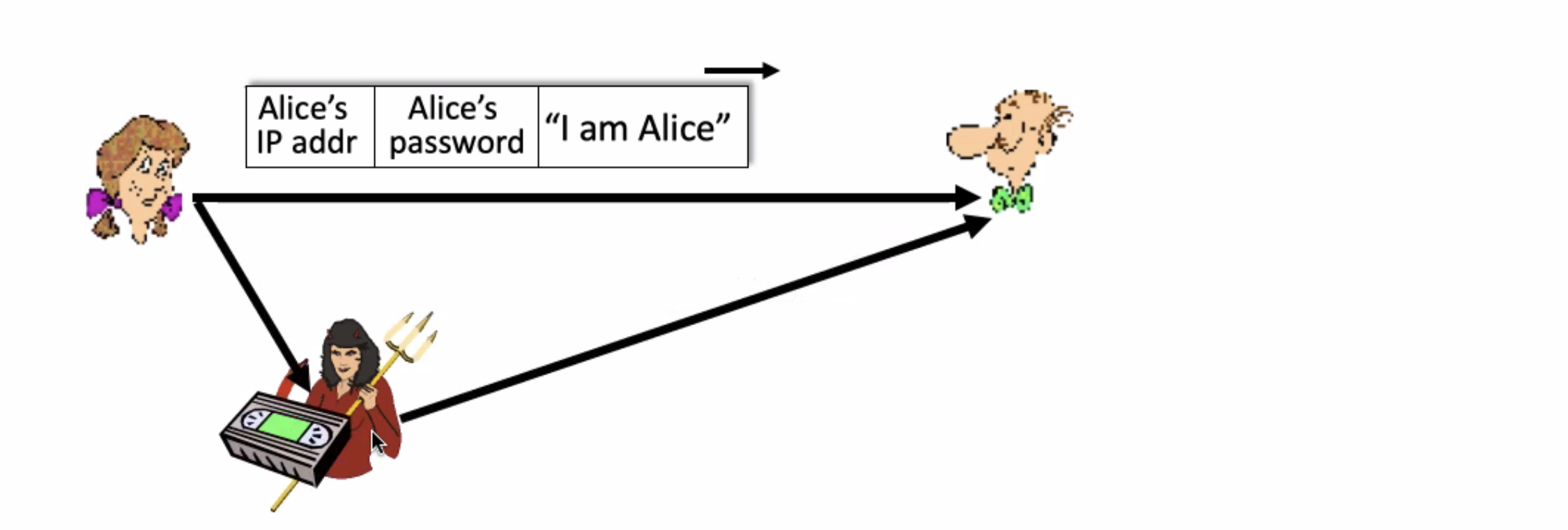
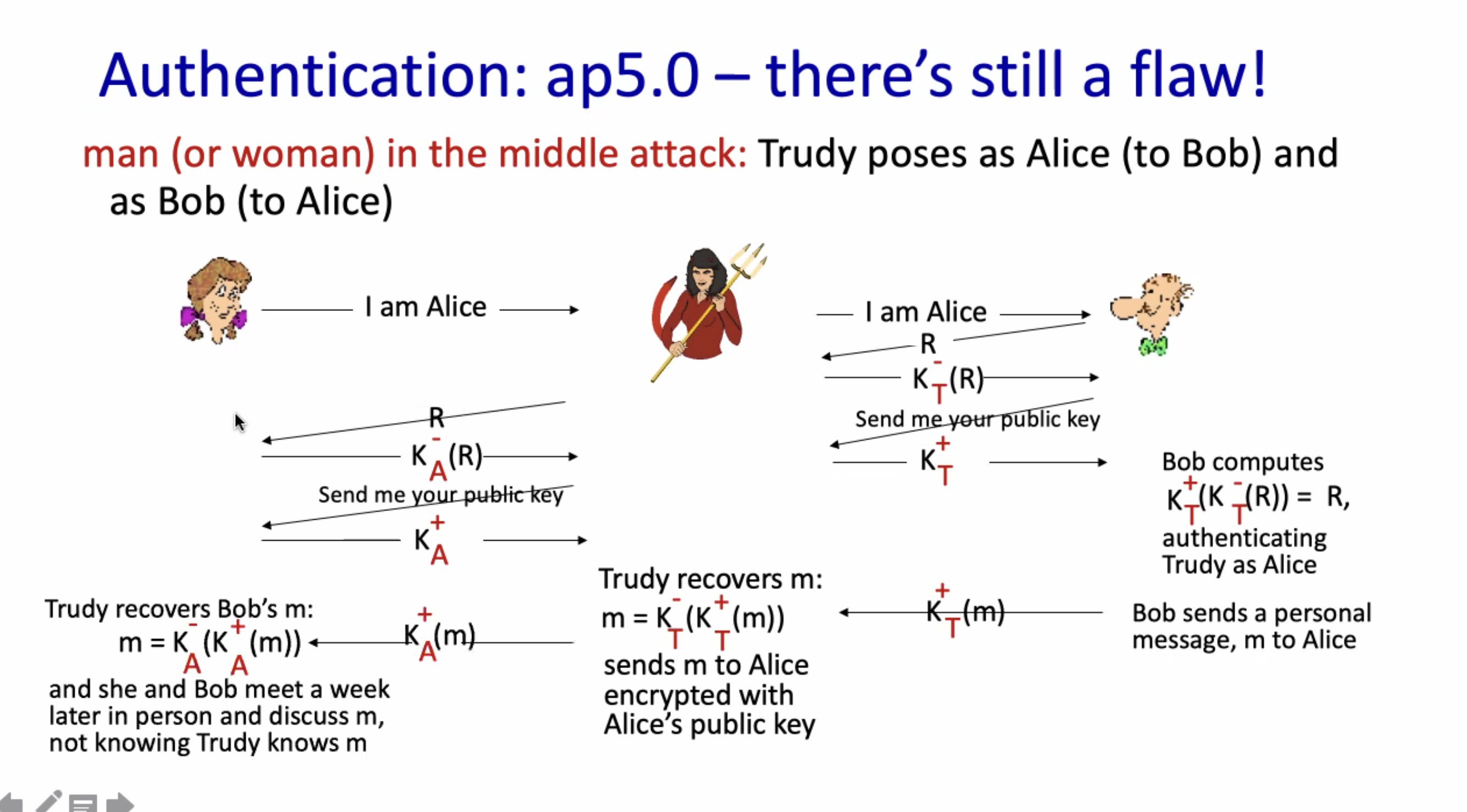
This still relies on the transfer of the symmetric key. Also, Bob can spoof himself as Alice, and vice versa.
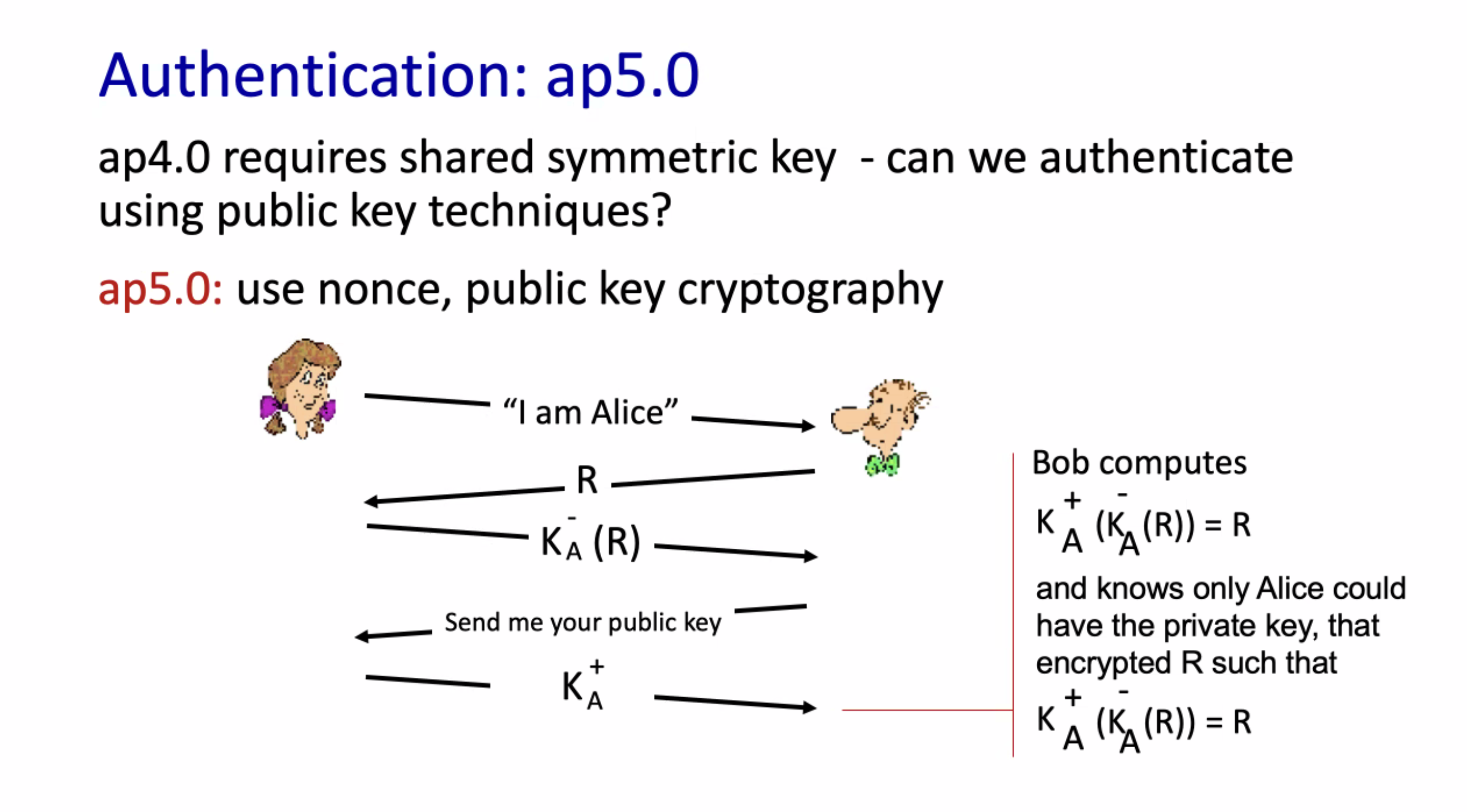
Here, anyone could create their own public/private key combination to respond to Bob.
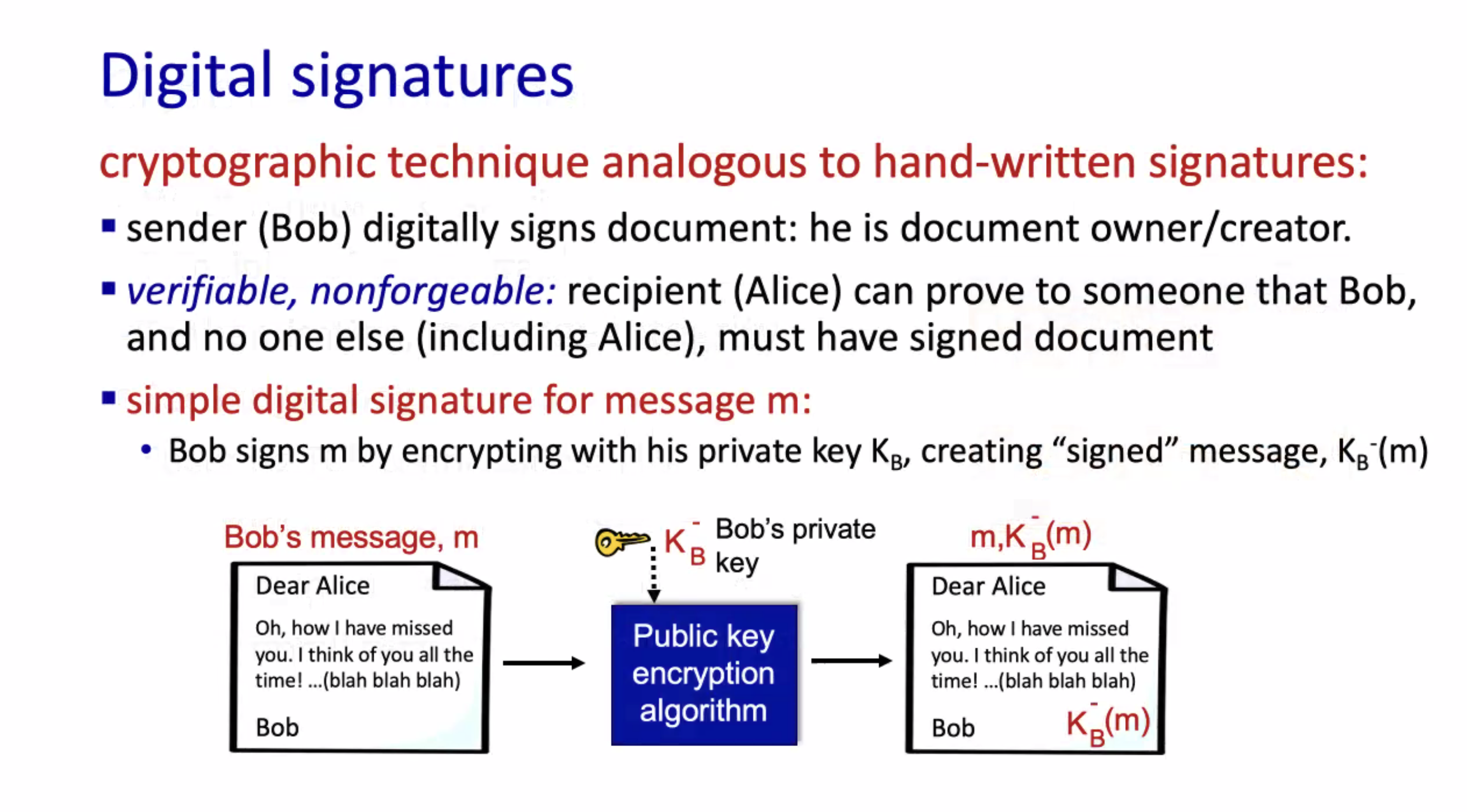

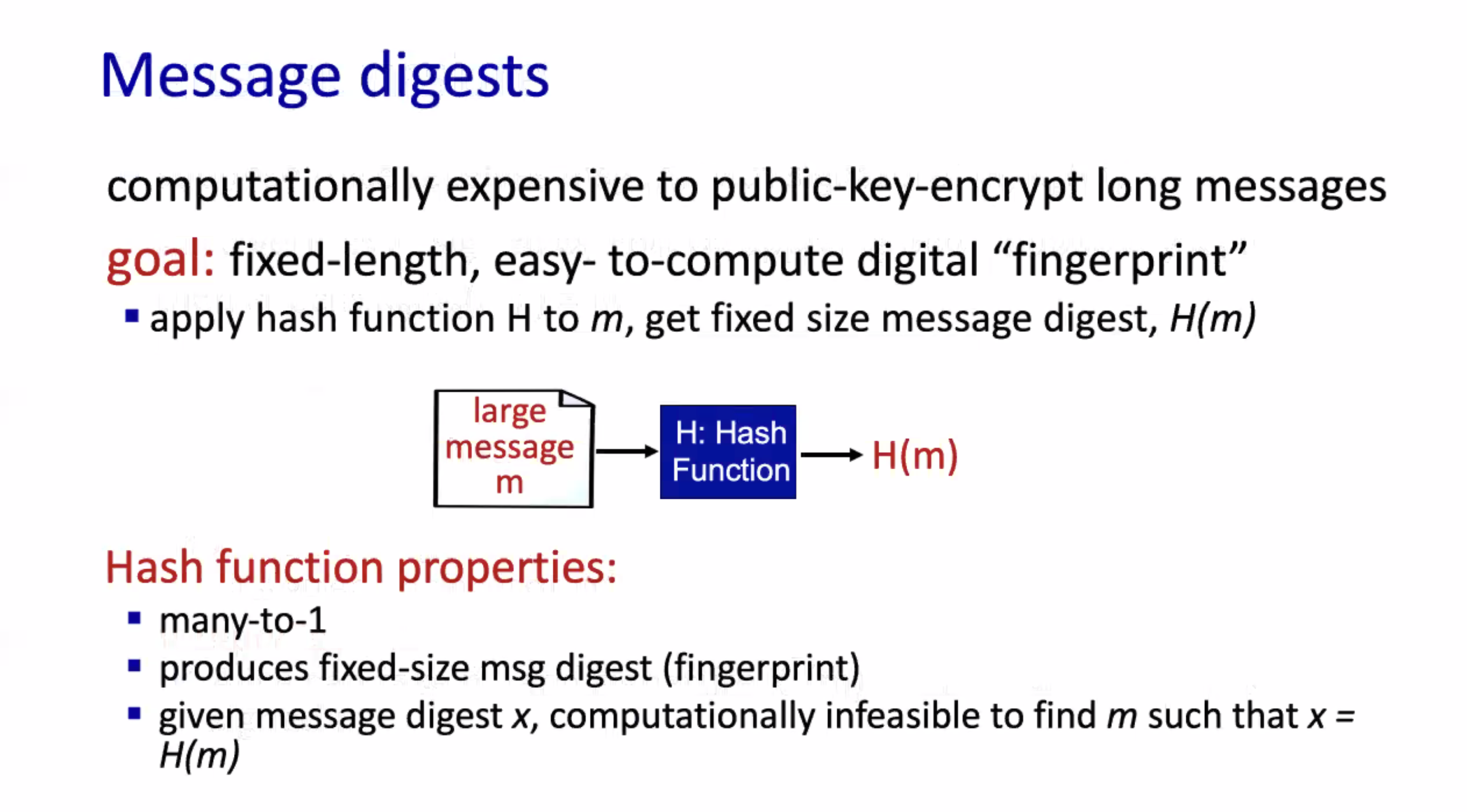
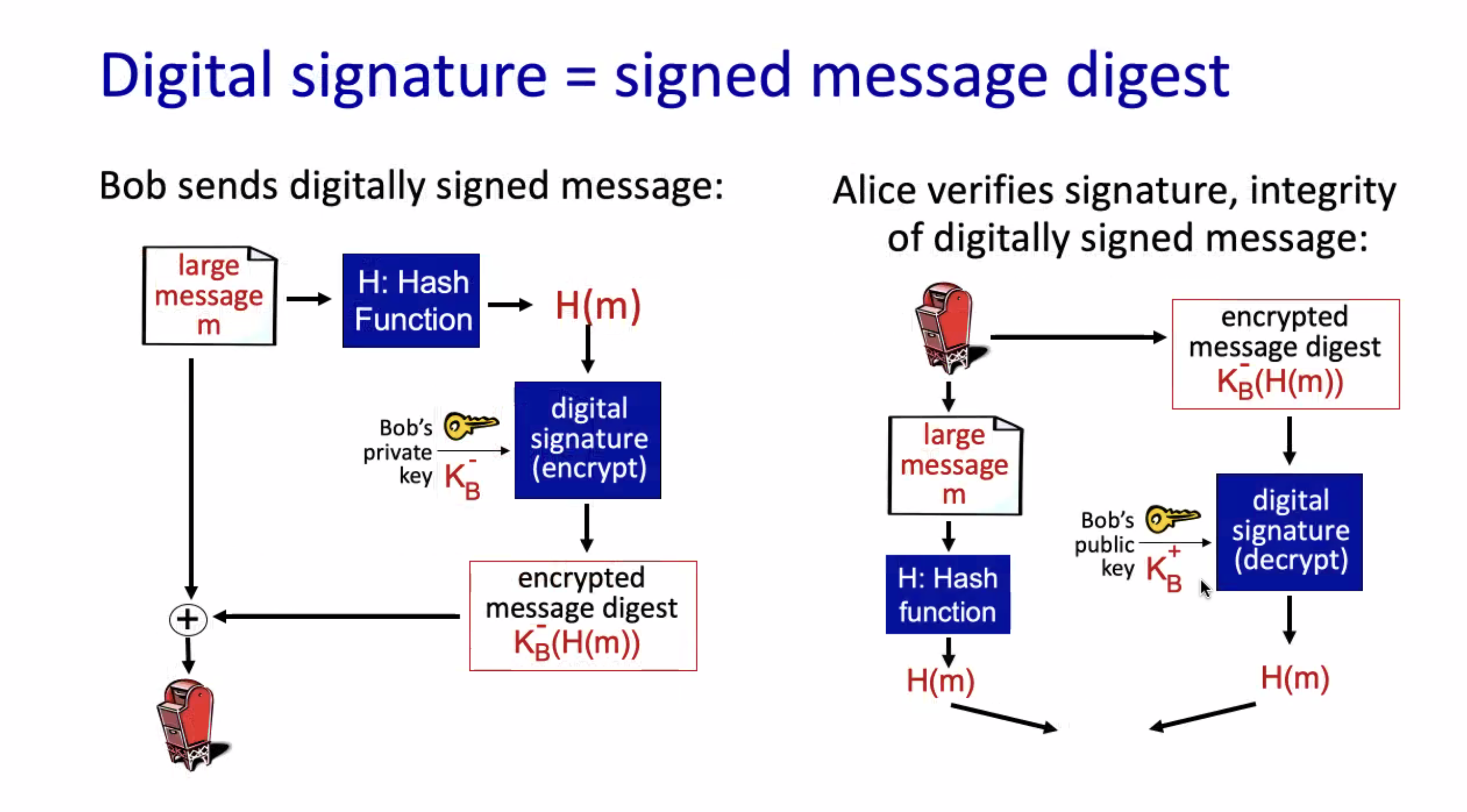

Hashing \( m_1 \) should not equal to the hash of \( m_2 \) , however it is possible. Read more on MD5.
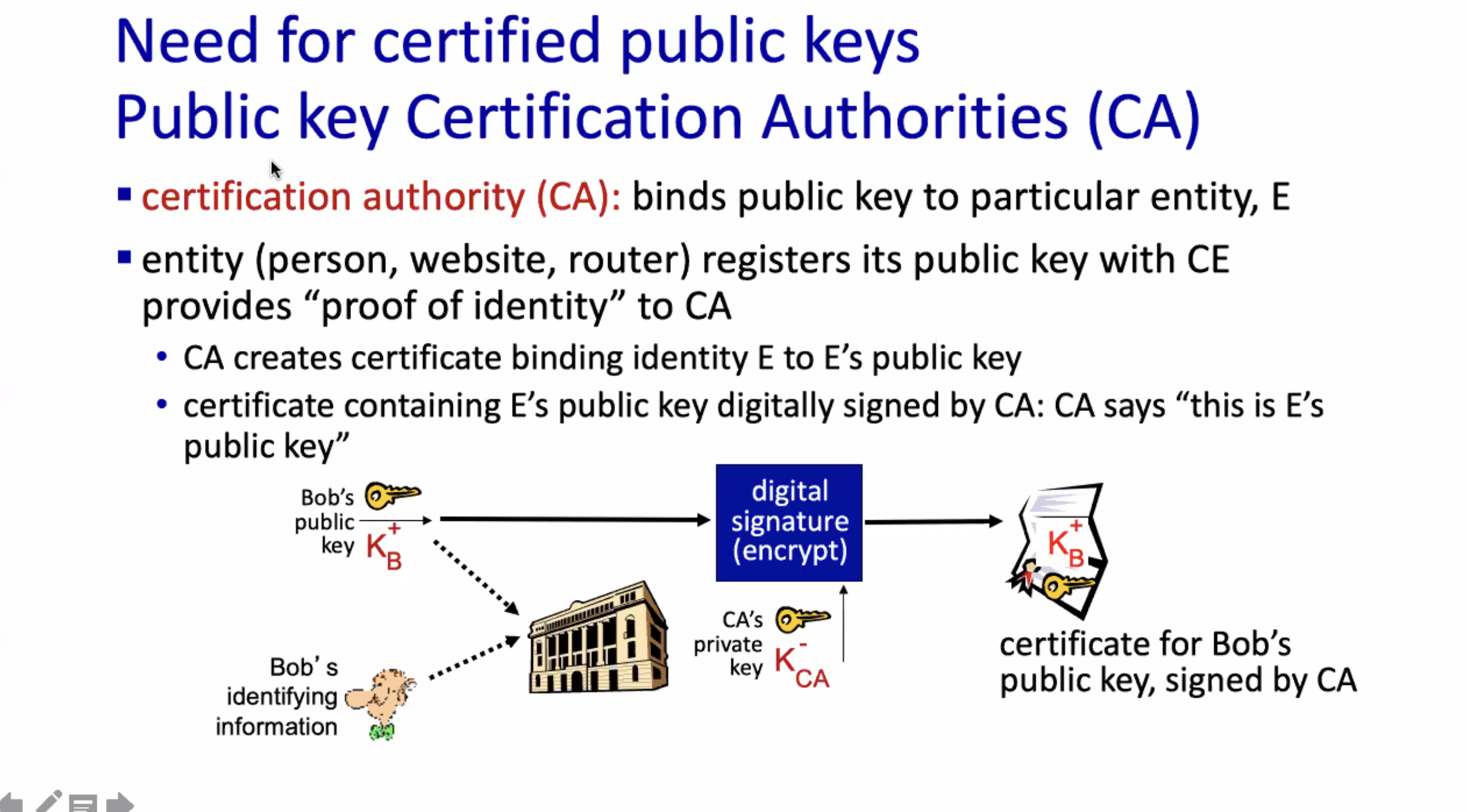
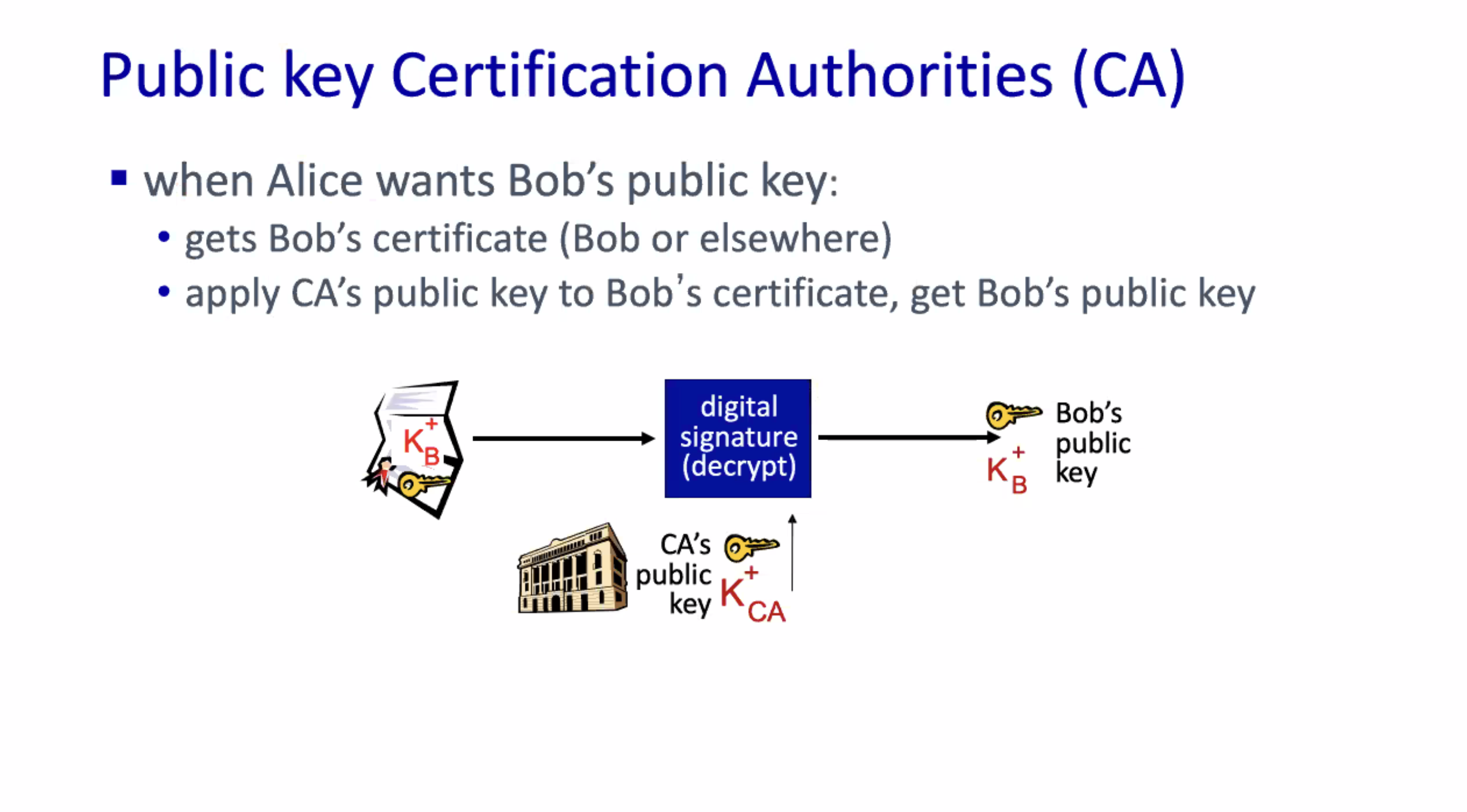
So instead of Bob asking Alice for her public key, he should ask for her certificate.
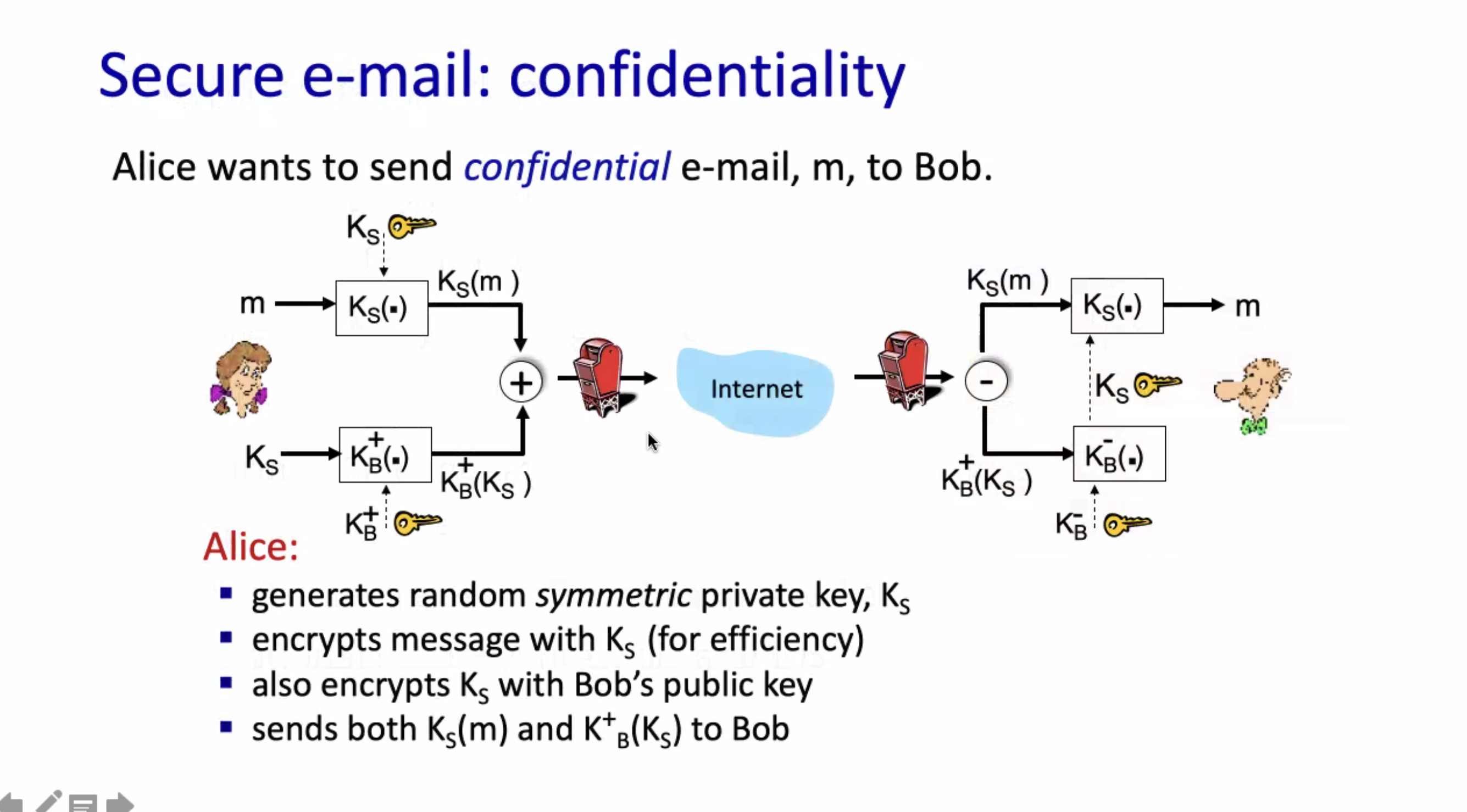
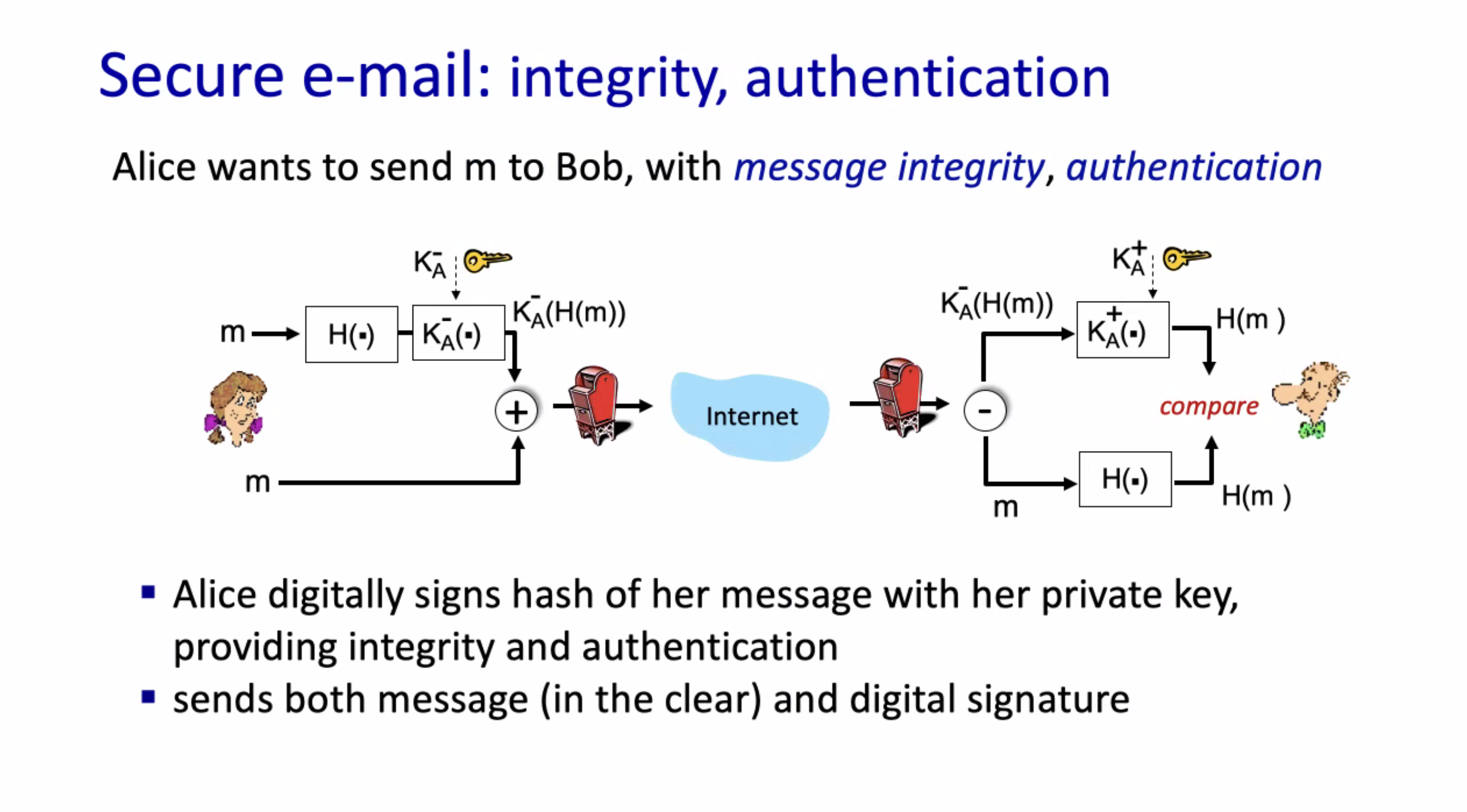
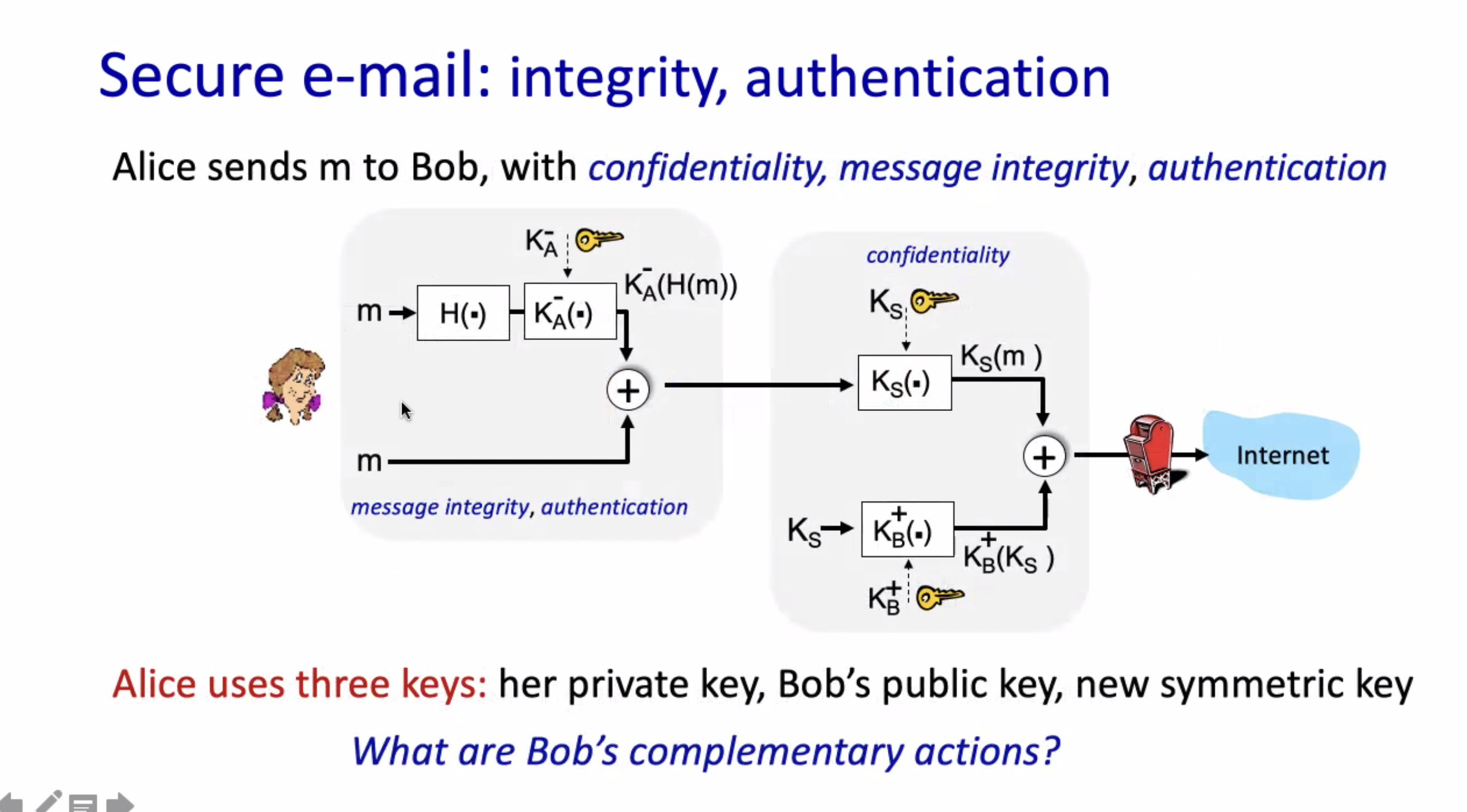
Securing e-mail #