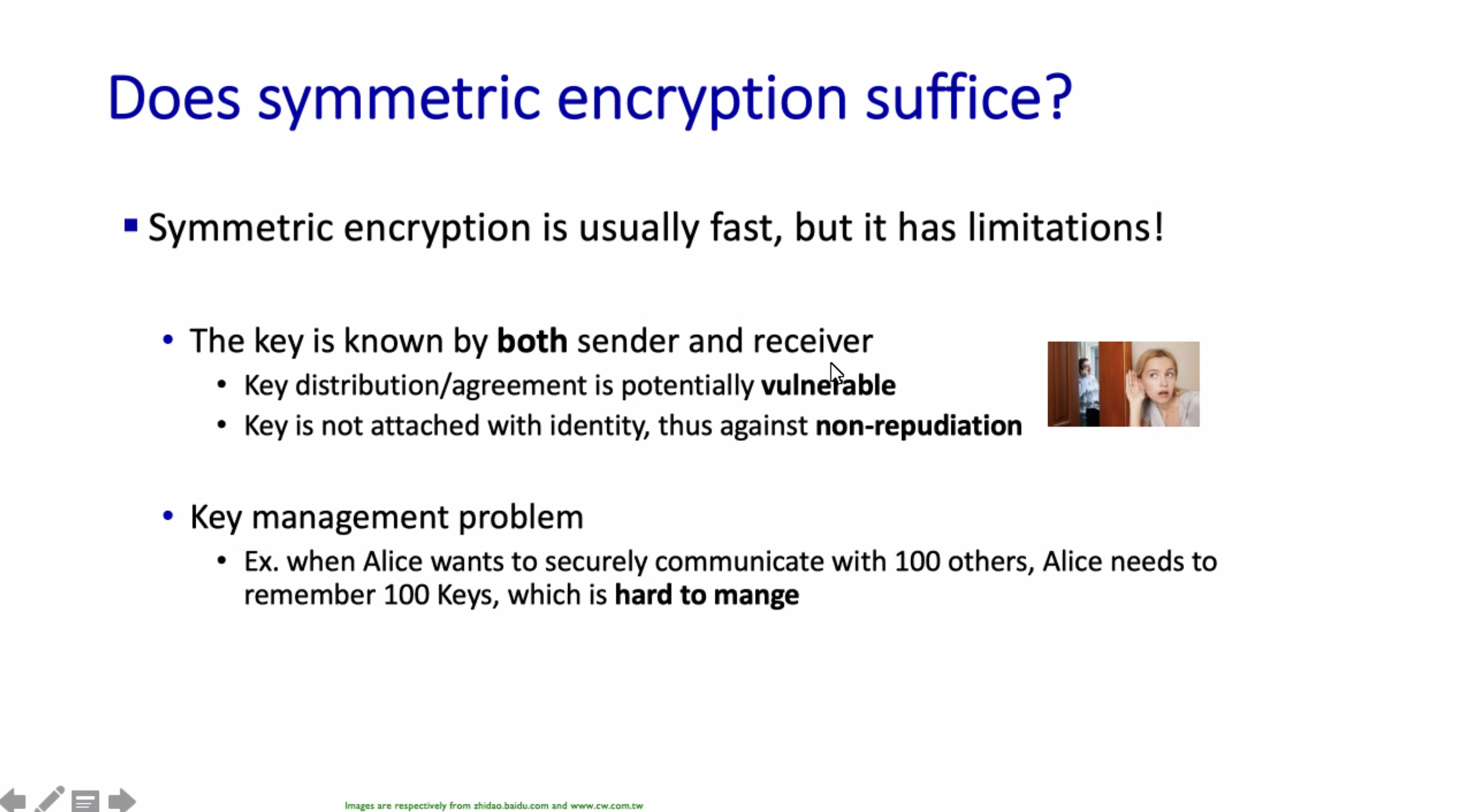
Network security #
What is network security? #



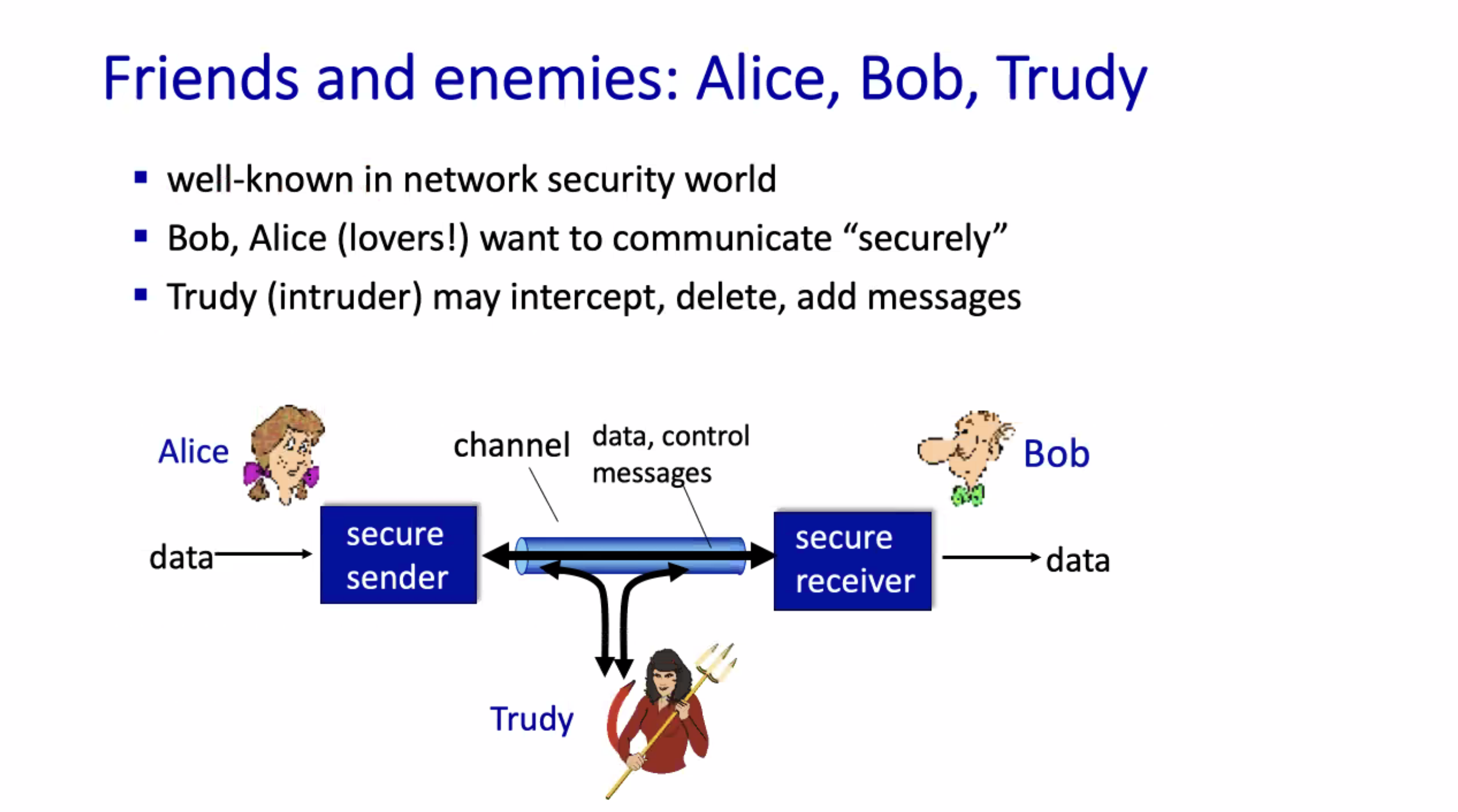


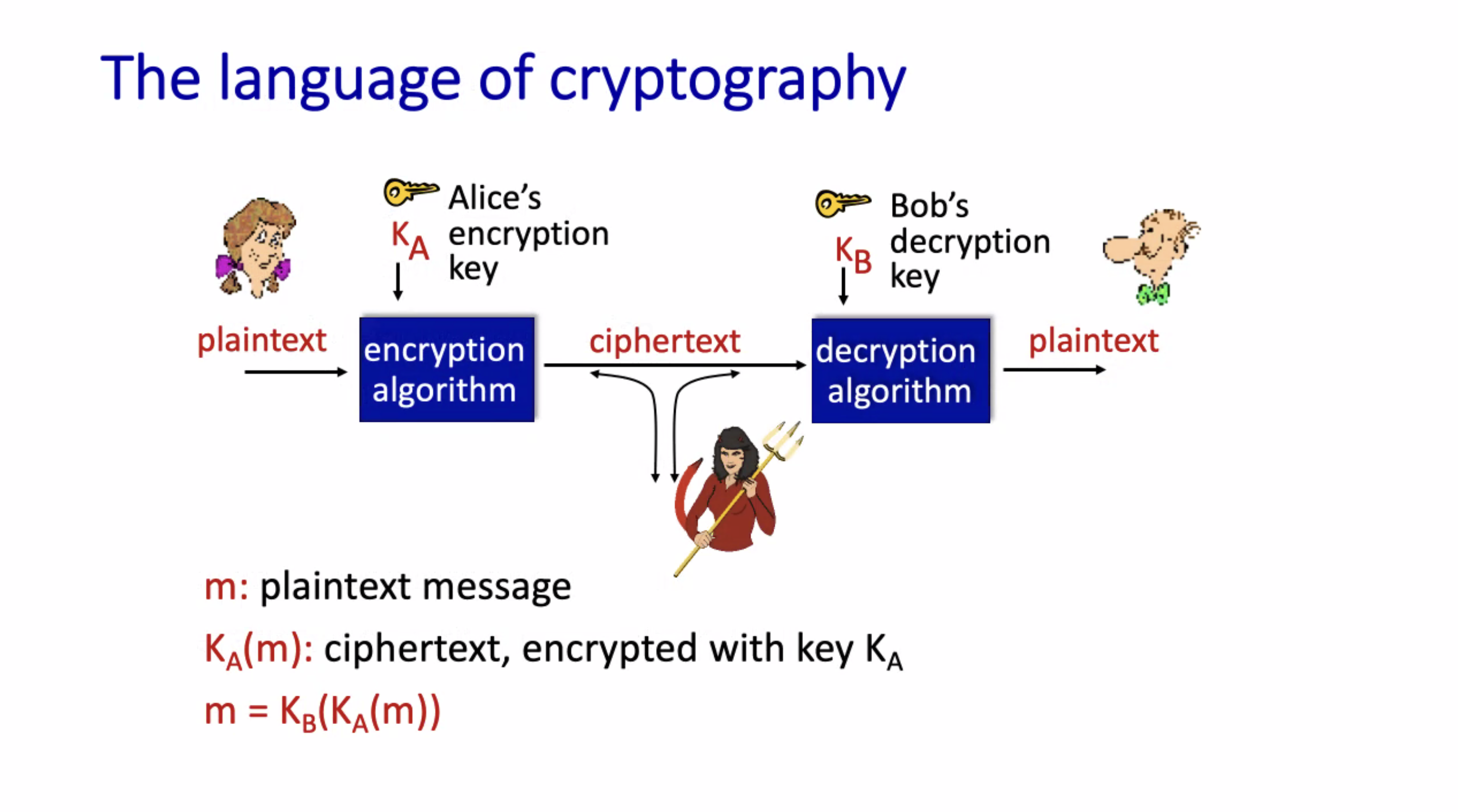
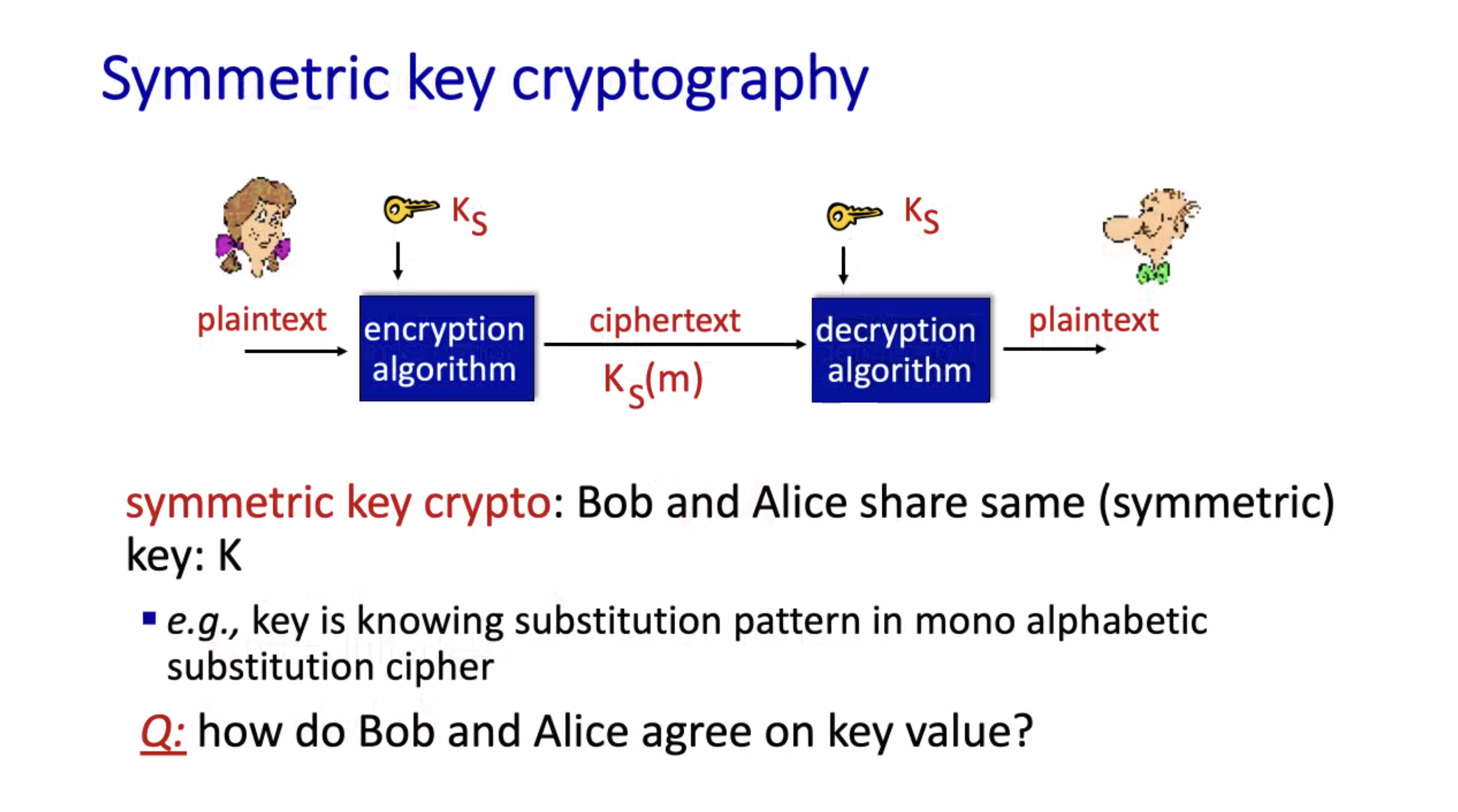
Cryptography #



RSA #
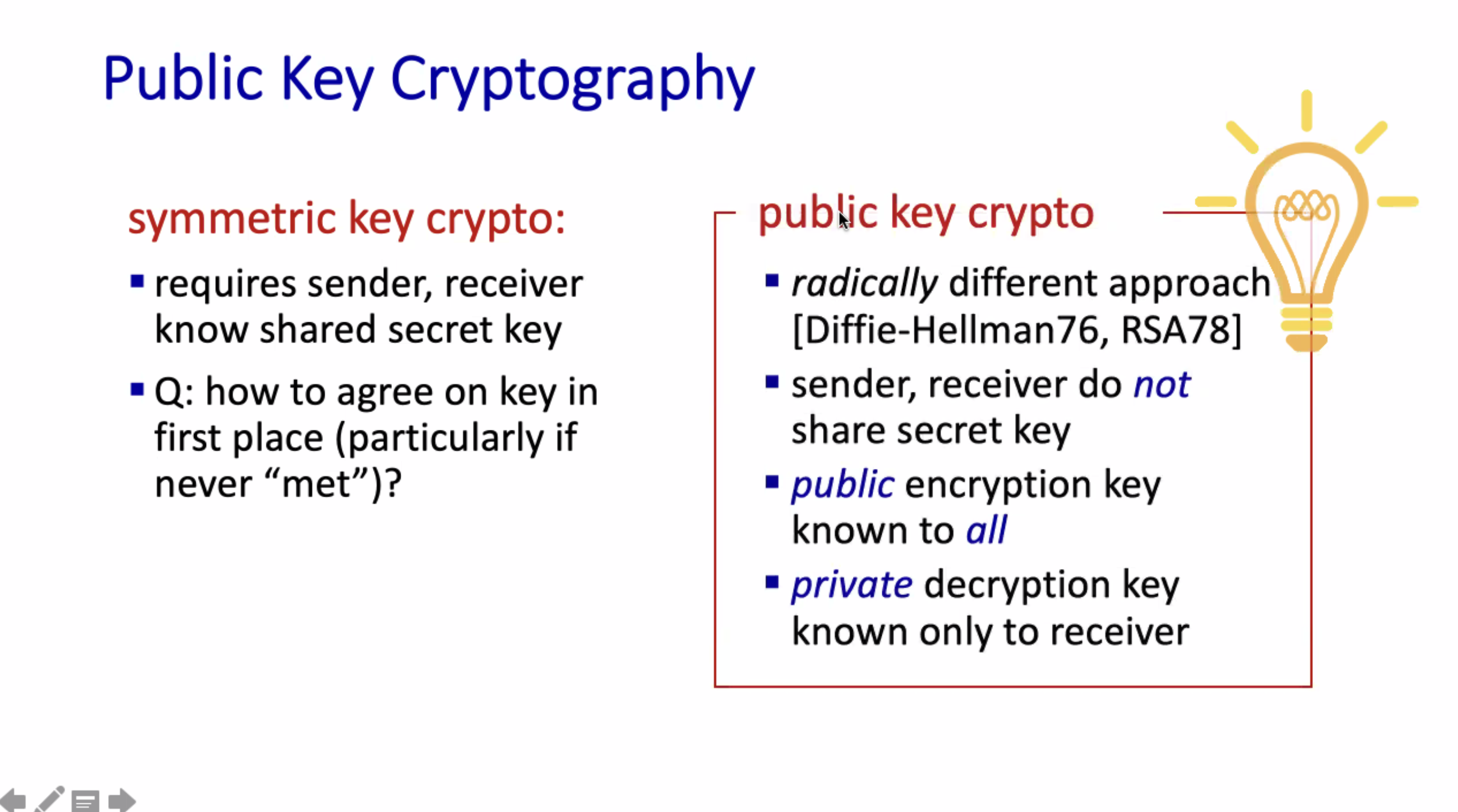
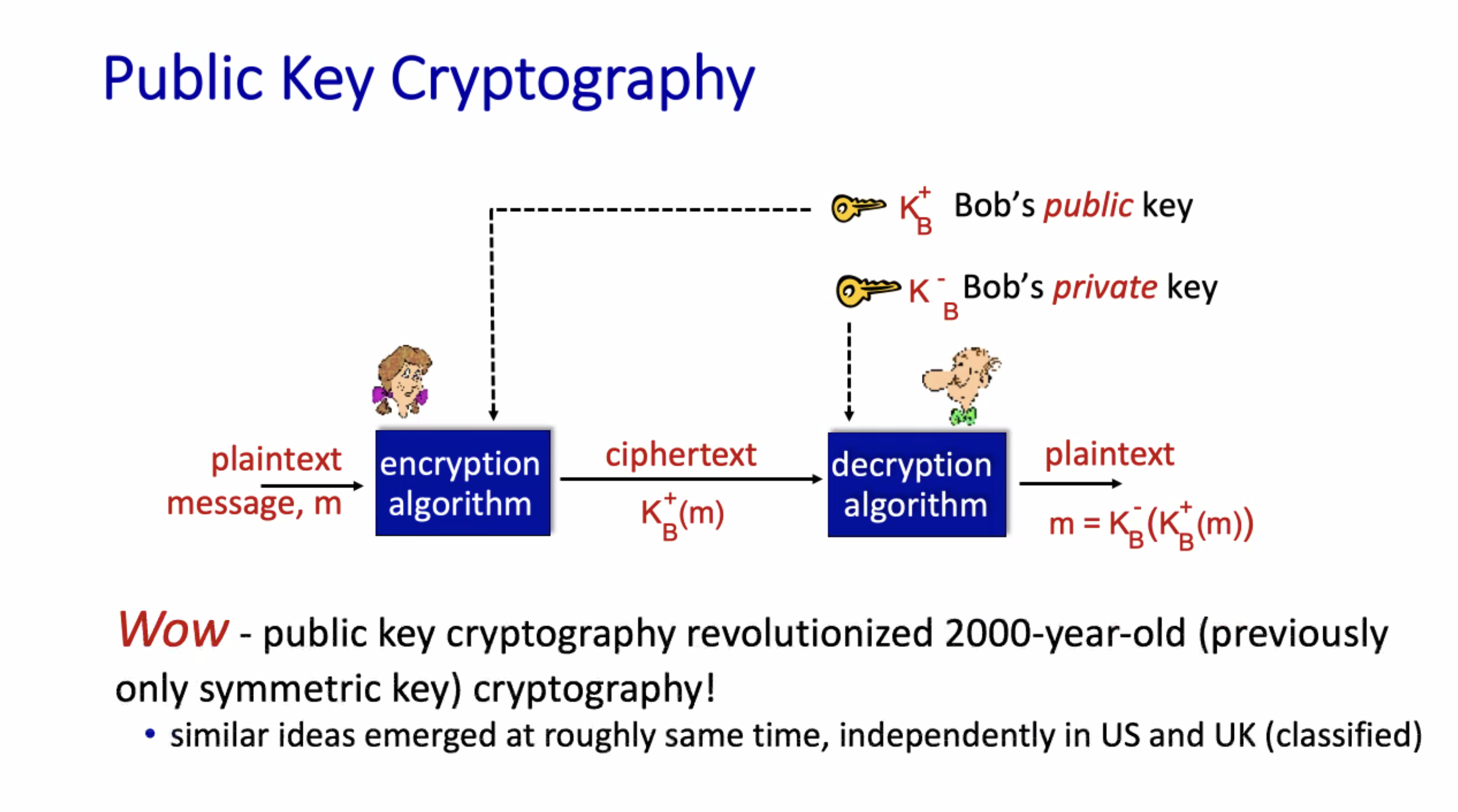
+ = public, - = private
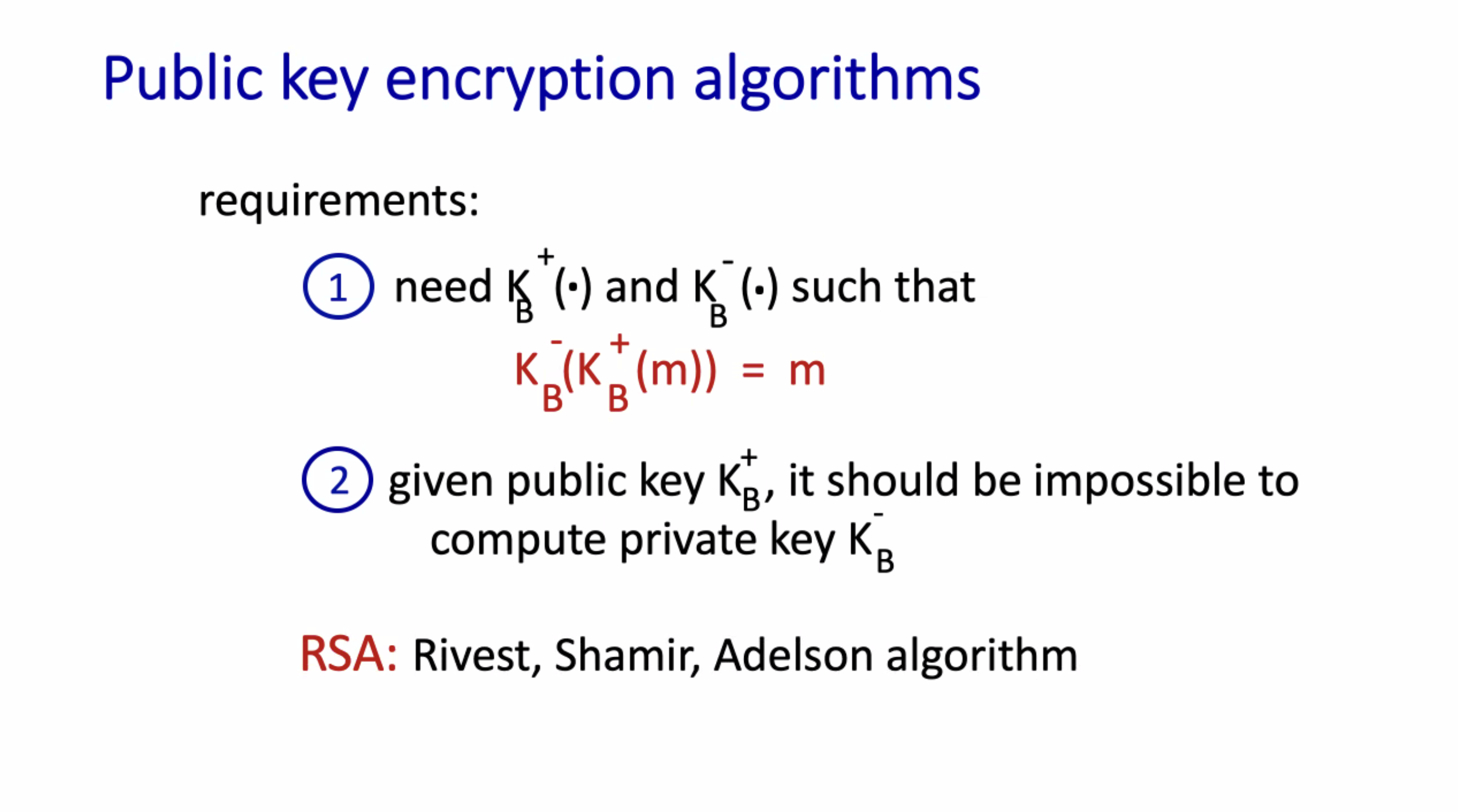
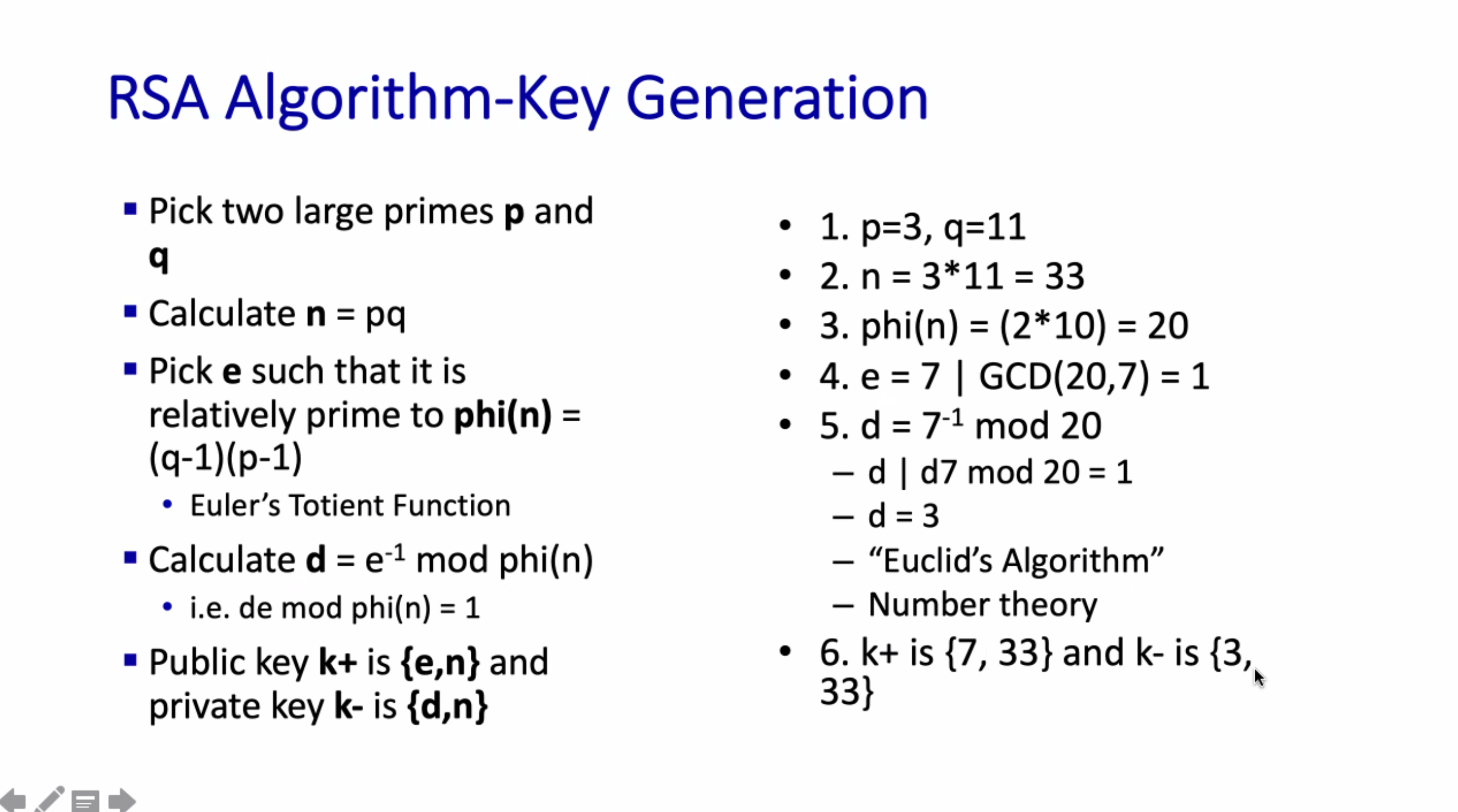
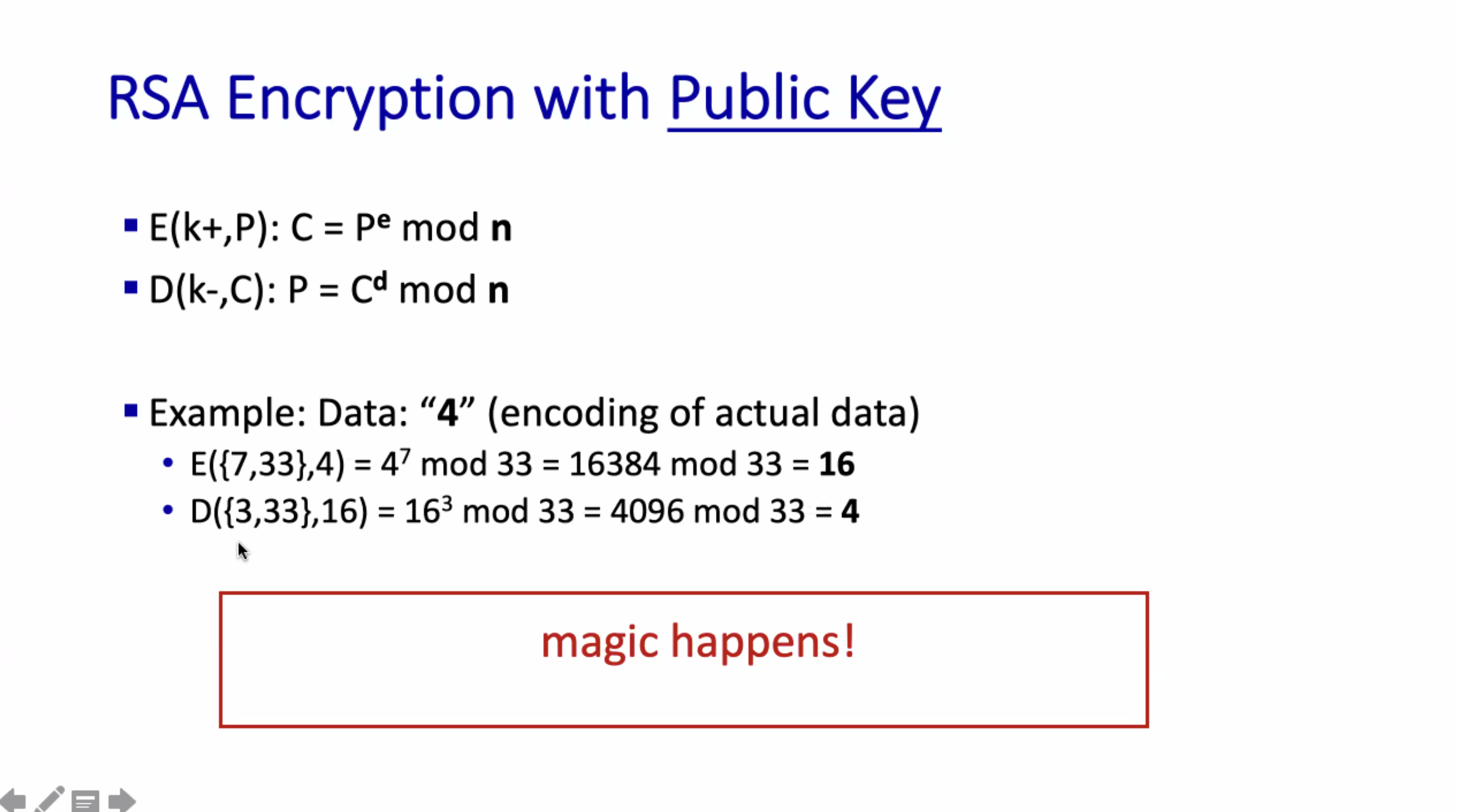
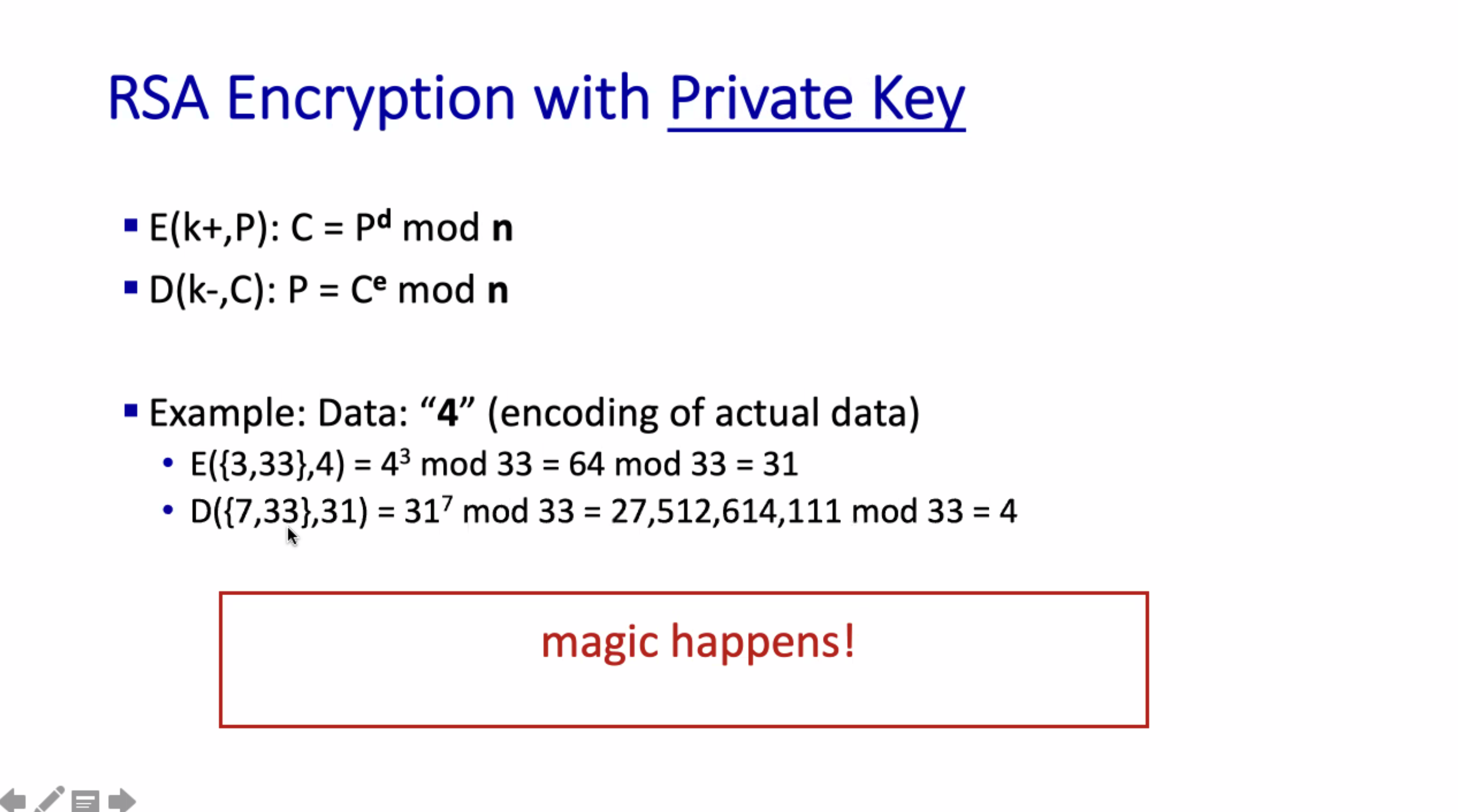
Given the public key \( K_{pub} \) and the private key \( K_{priv} \) , we can decrypt anything encrypted by the public key, and vice versa.
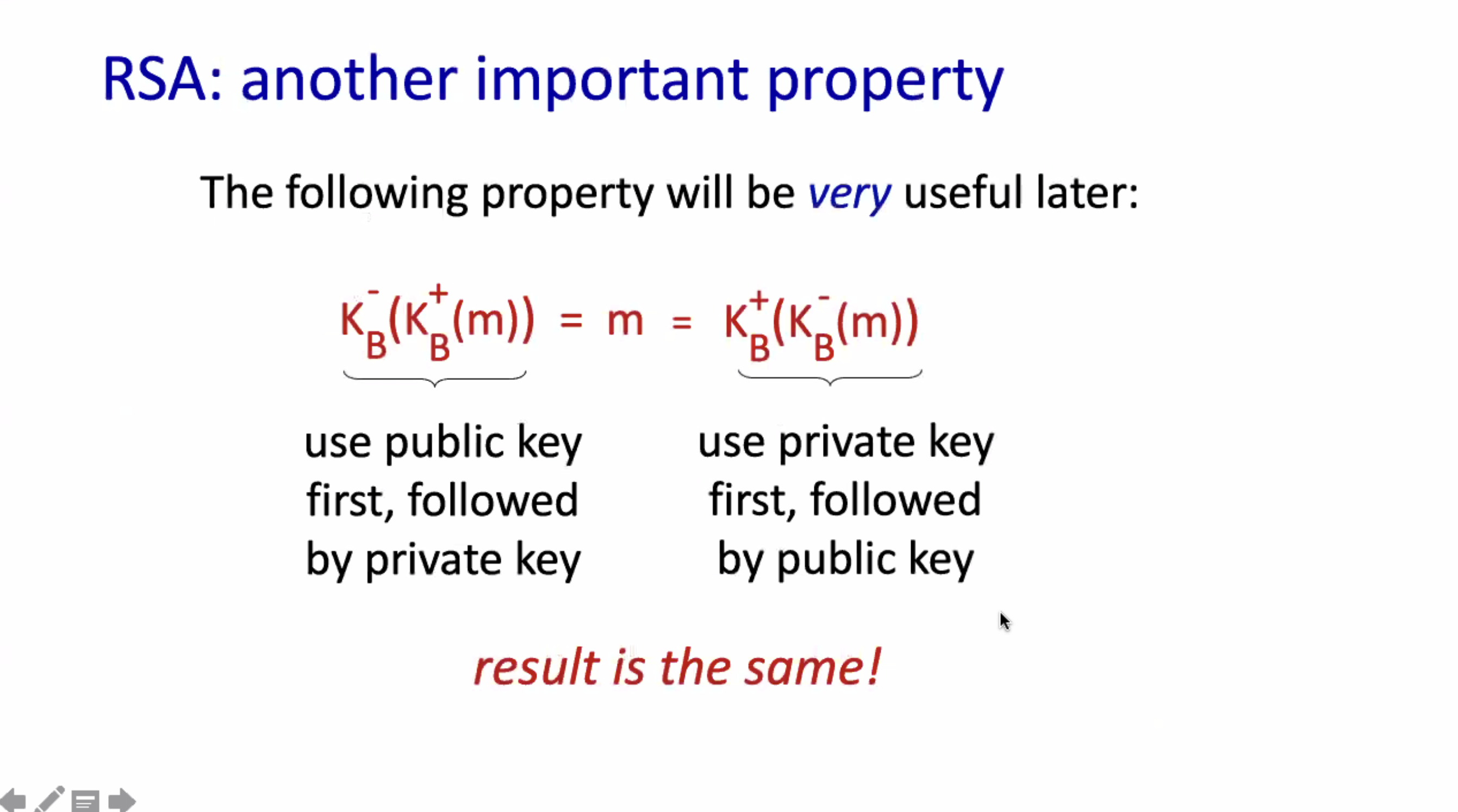

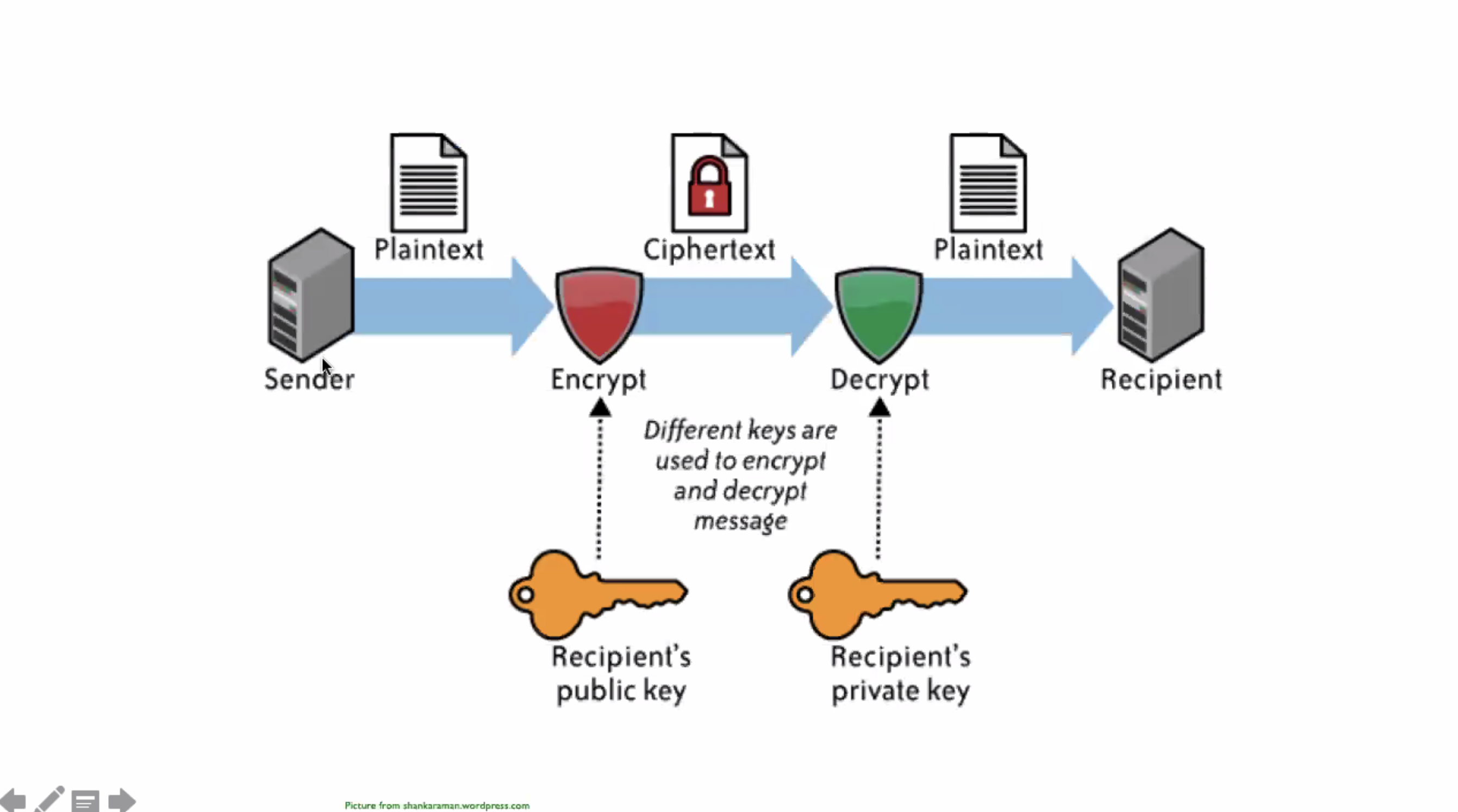
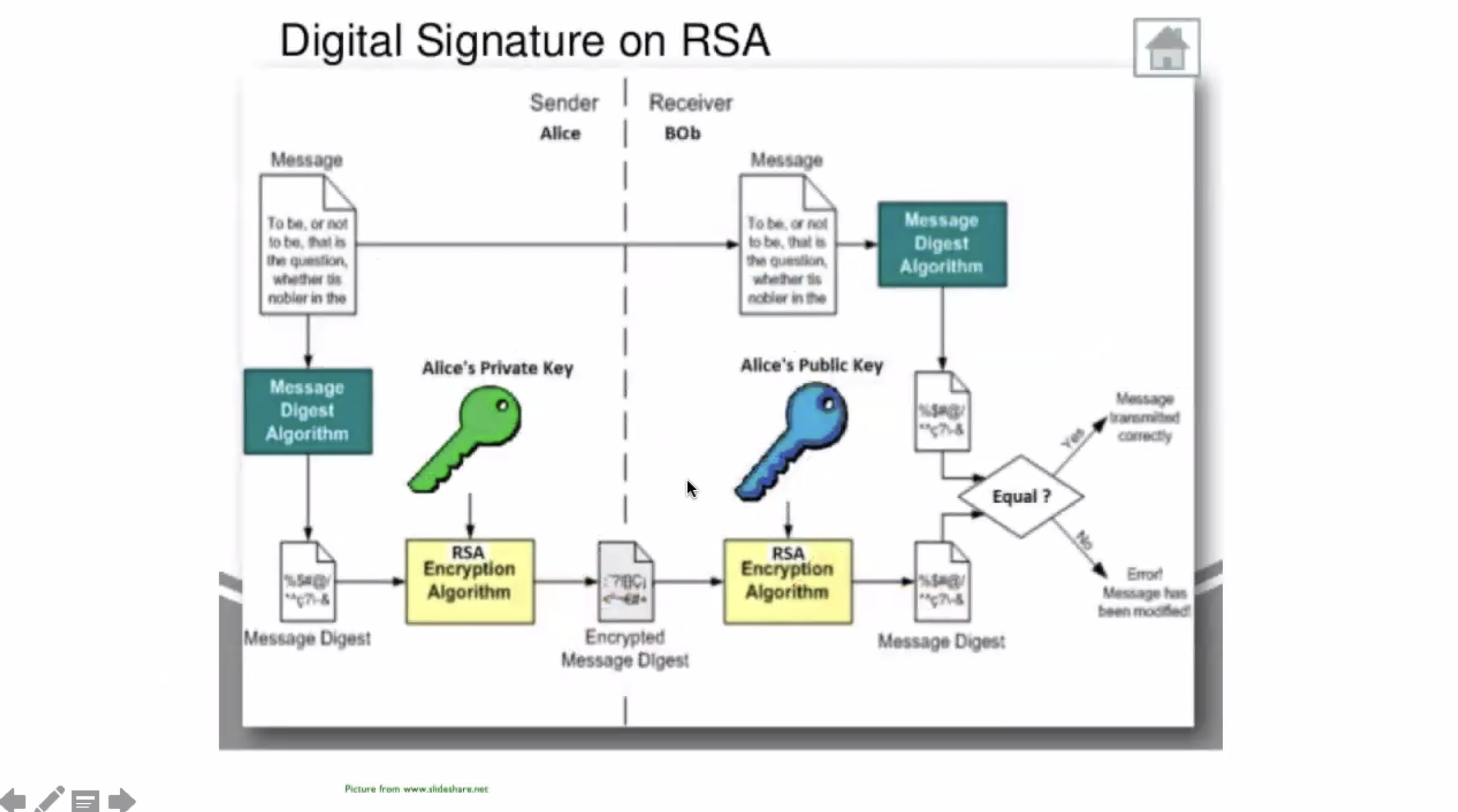


Alice invents a symmetric key, and sends it to Bob using RSA encryption. That way the computationally slow RSA algorithm can be used to send the symmetric key, and the symmetric key can be used for continual encryption. This speeds up the overall encryption algorithms for large amounts of data.